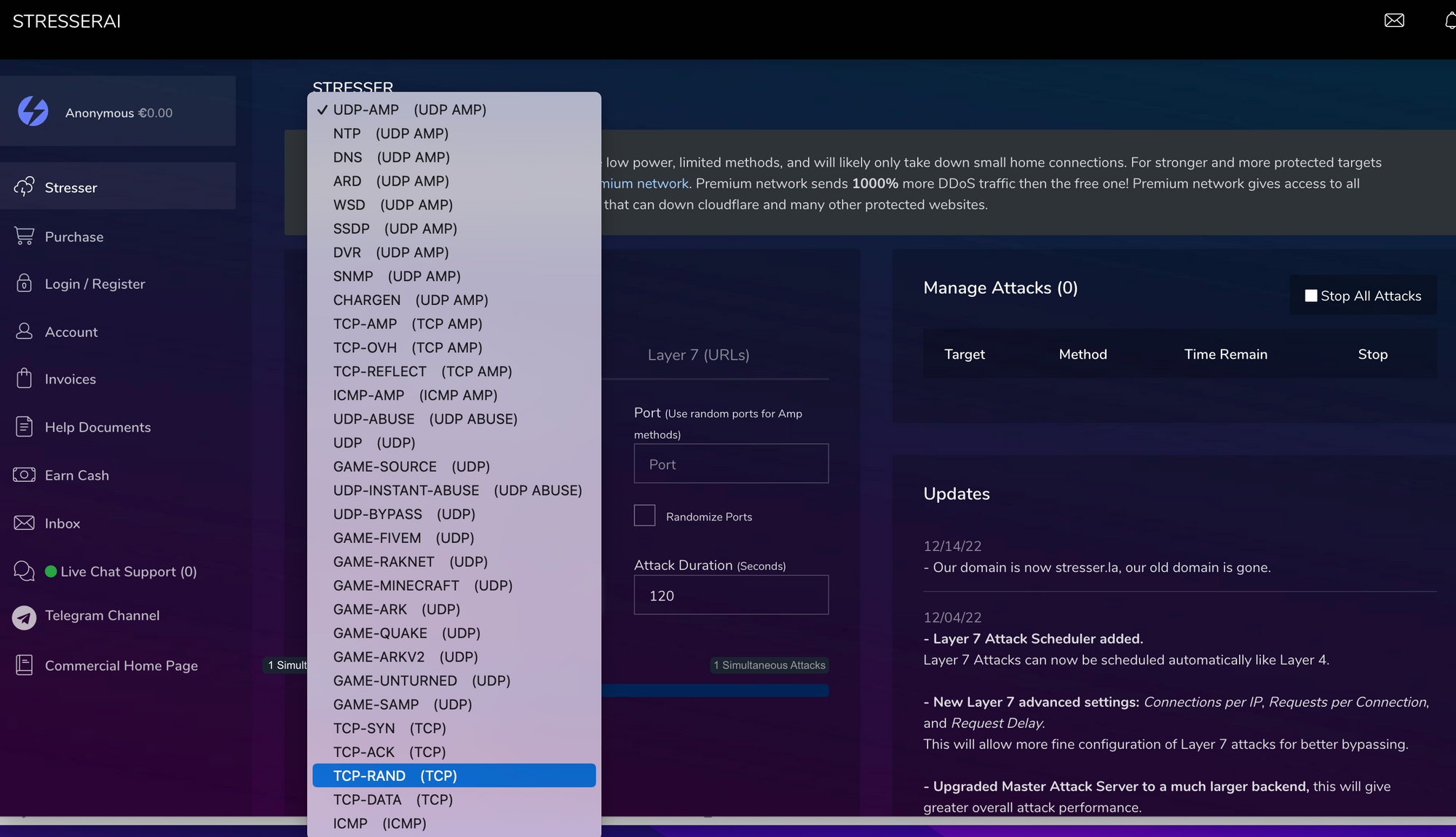
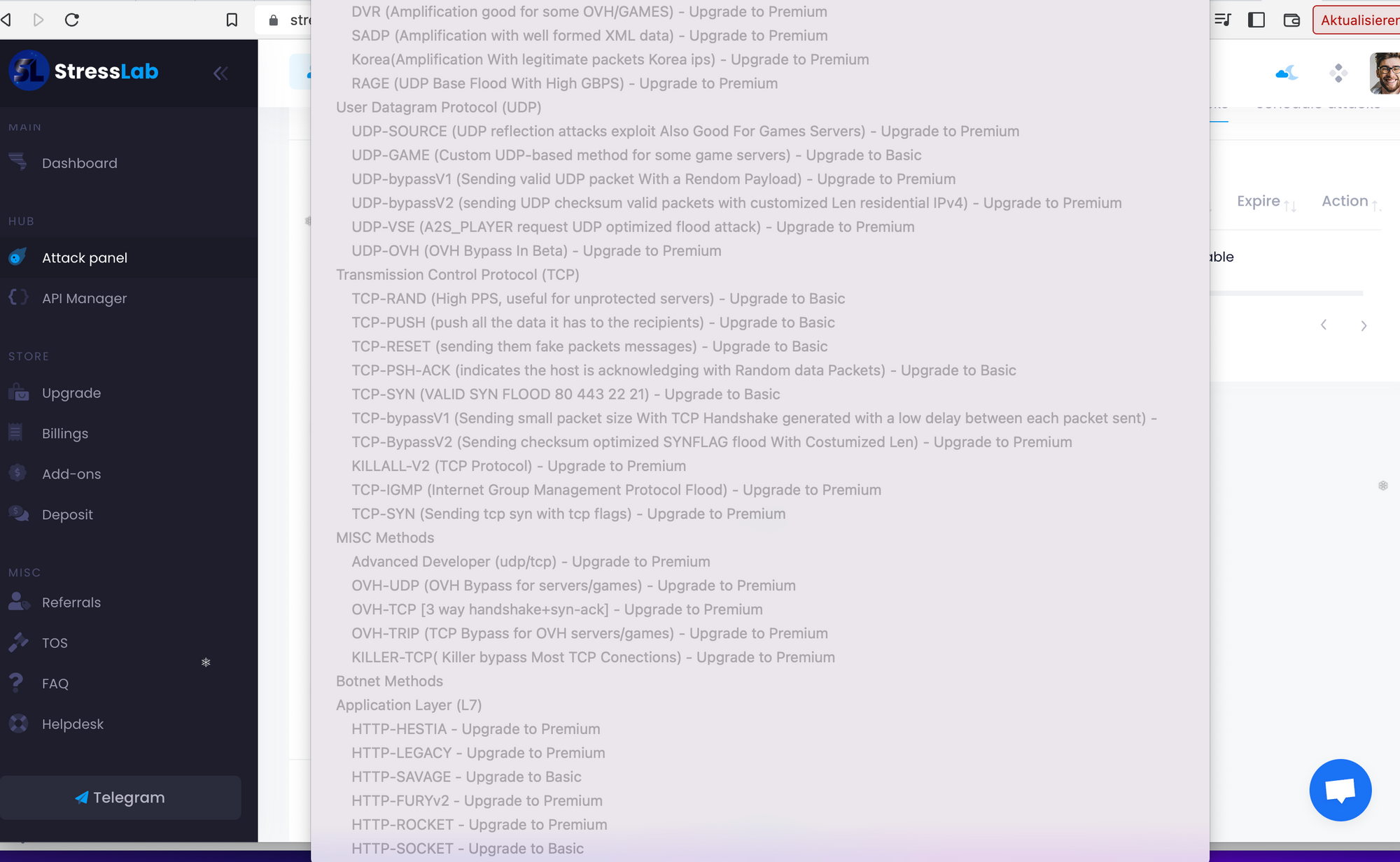
Some new methods and capabilities have been observed coming to booter-services in the last year, that have been used only by more advanced attackers:
- Browser-based attacks to mitigate BrowserChallenges
- a wide range of TCP-based attacks, which use is also reflected by a) TCP beeing the mostly-observed attackvector on network-based attacks in 2022 and b) beeing often successful and thus beeing applied by whoever executes DDoS-Attacks; we covered this developmend in our post "Smashing the Stack for fun and Profit,m 2023 Edition"
please find below a couple of recent screenshots from booter-services and available attack-methods



💡
What does that mean for Companies and Organisations under DDoS-Threat? You should implement tests that are able to simulate those attacks which are available and widely used, in order to make a sure that your protection is well-tuned and capable to mitigate all sorts of DDoS-Attacks.
The bad guys don't sleep, and neither should you
The bad guys don't sleep, and neither should you
Member discussion: