TL;DR: just use free/paid Proxyfarms and Browserbots. Thats it. Thats the News. Find explanation and possibe countermeasures below.
Inb4: Yes, this method (Browserbots combined with Proxyfarms) is known and became popular in 2022 with the armada of layer-7-frameworks and the wide usage of geofencing, see screenshots below. We are also aware of frameworks using public lists of proxies like CC-Attack, KARMA-DDOS and MHDDoS.
Google-Team is aware of it
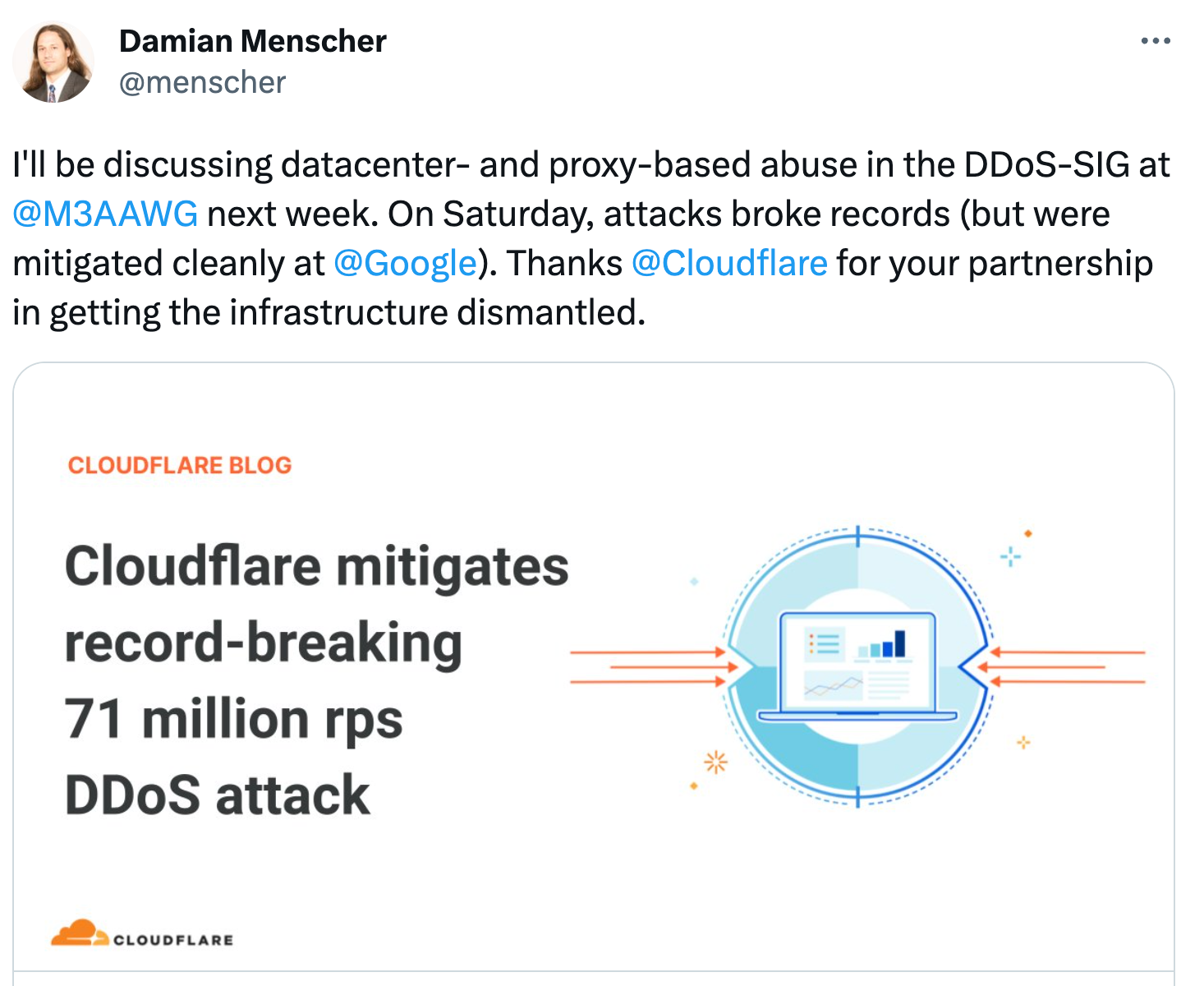
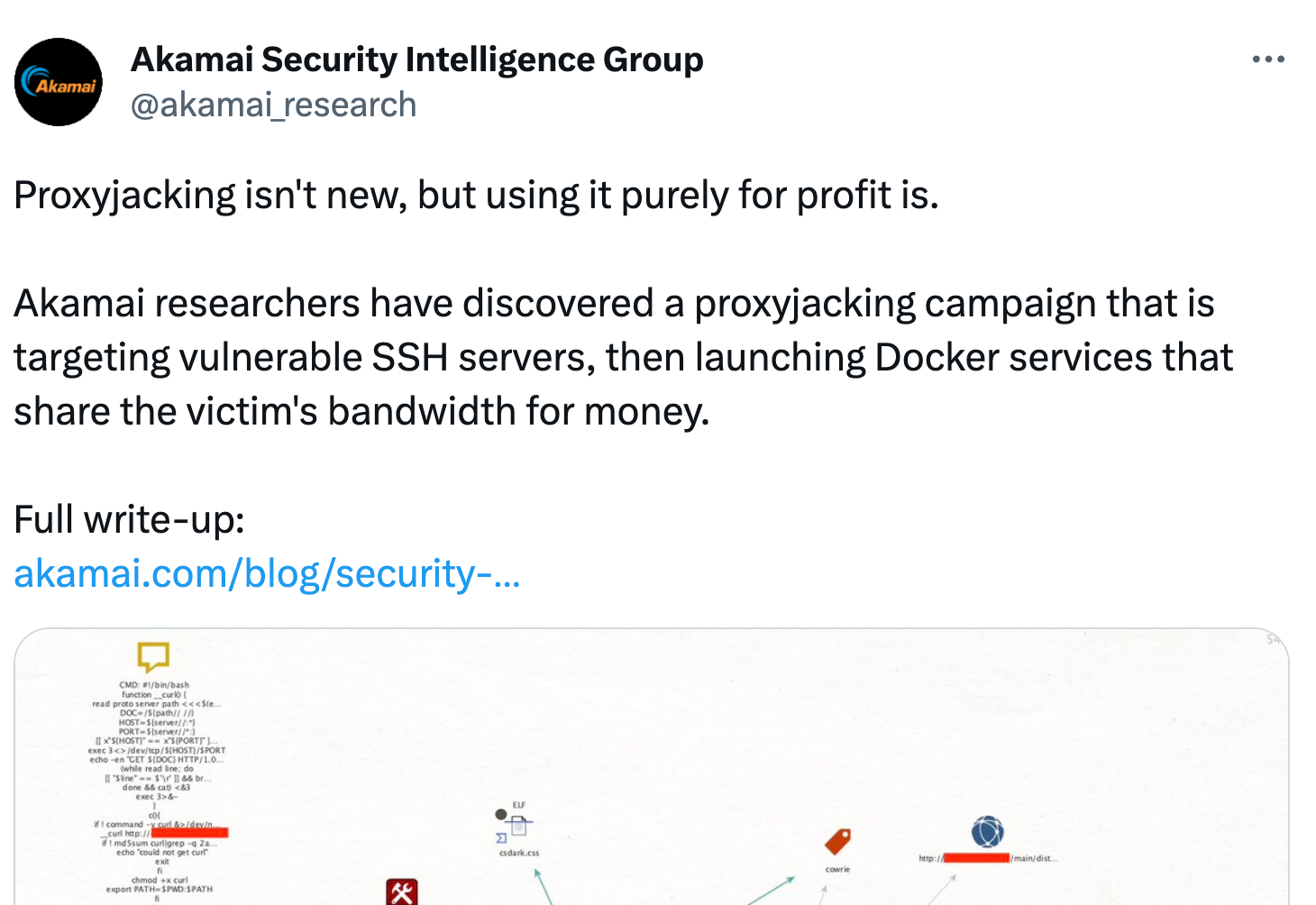
Akamai released an analysis of proxyjacking Botnet
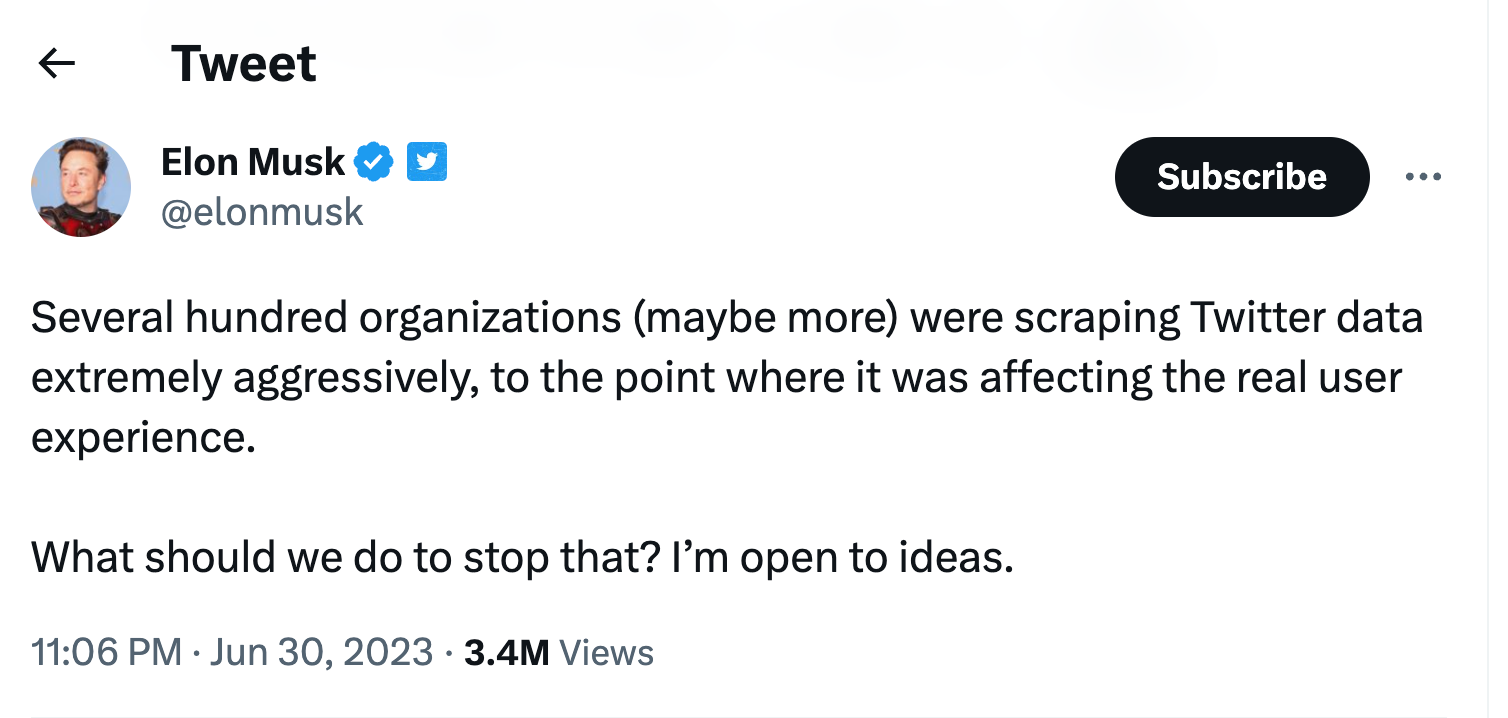
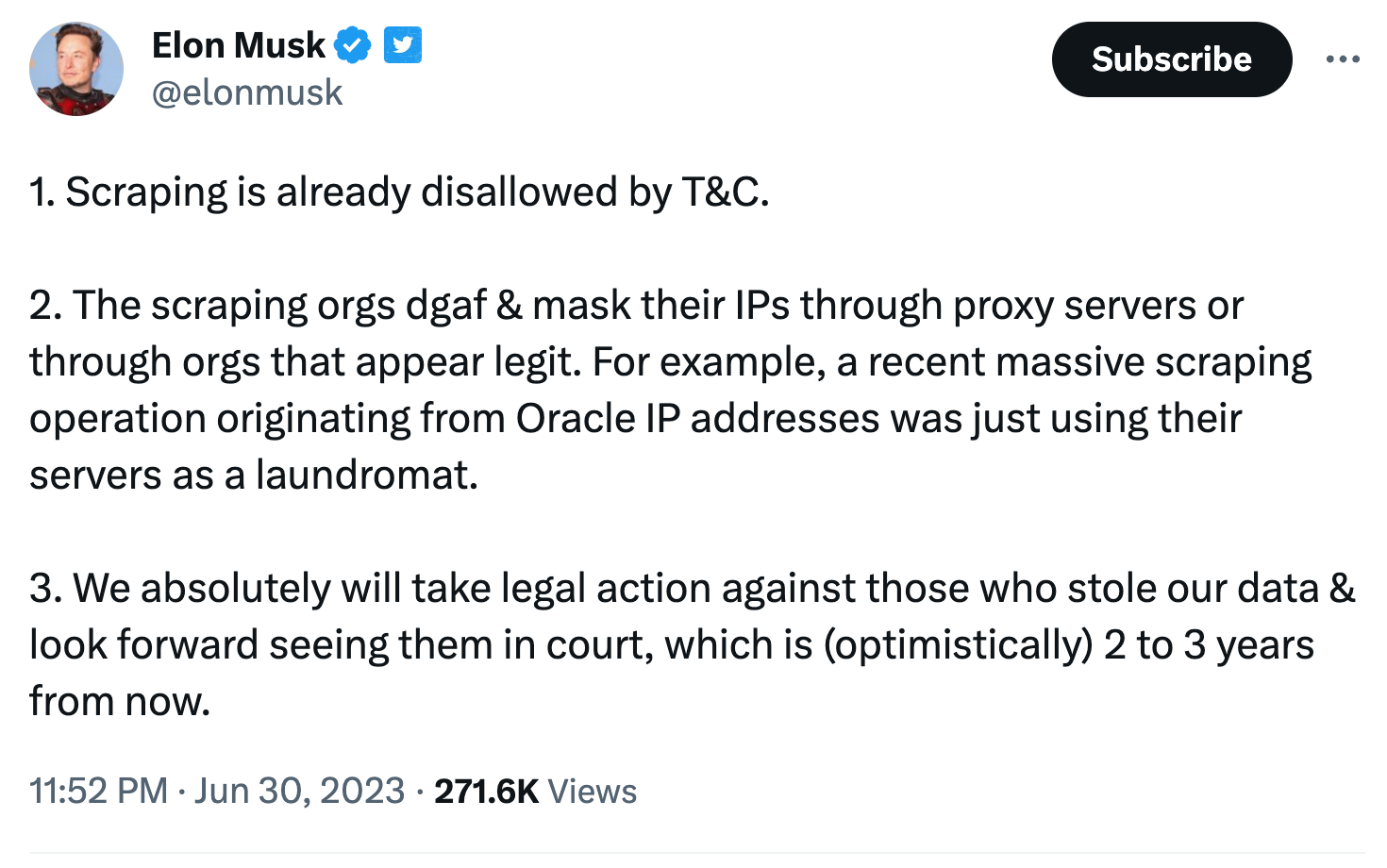
Also Twitter seems to have issues
Also Microsoft
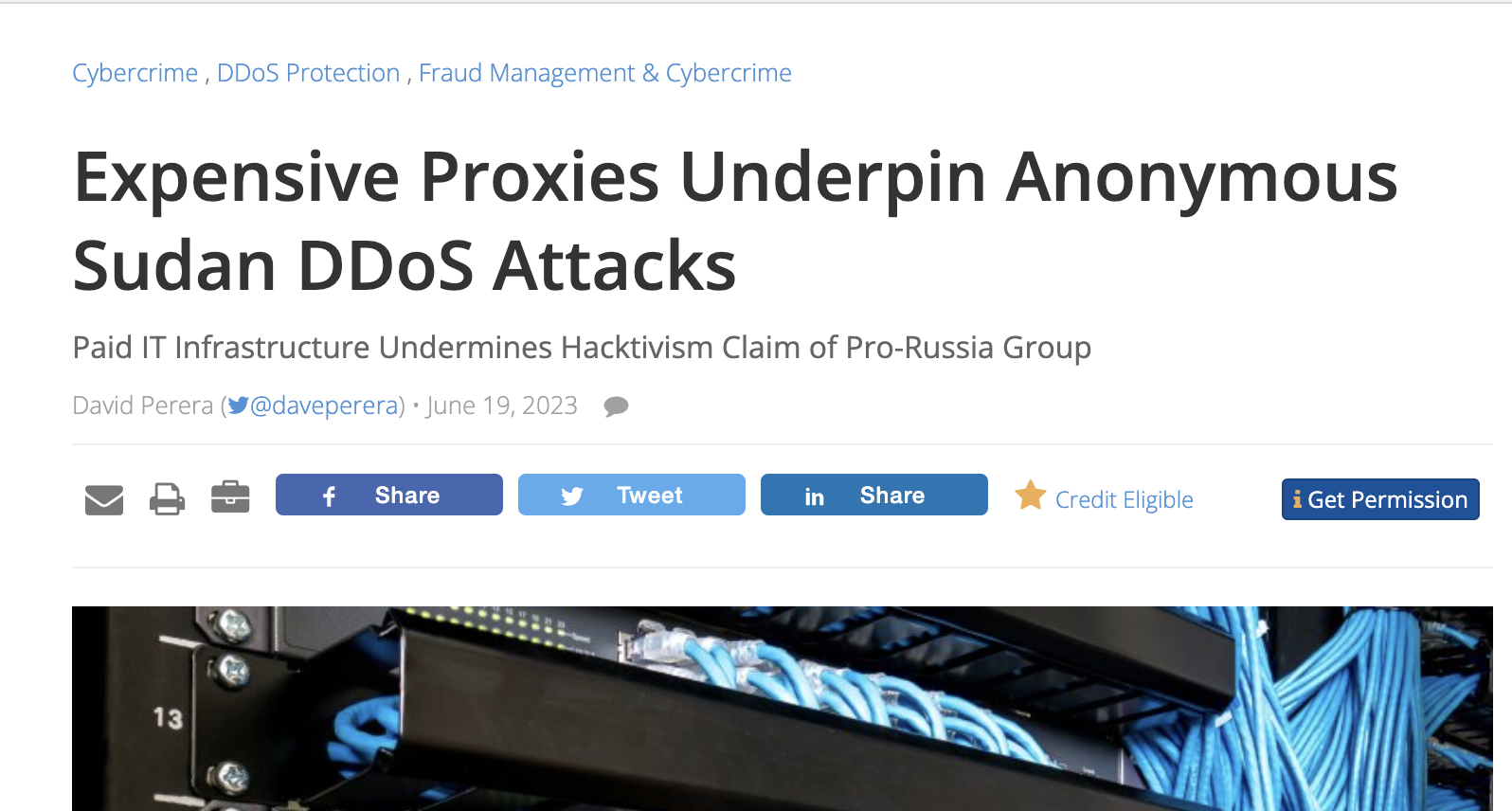

Bypassing explained
Layer 7-based protection mechanisms are based on various methods, which can be easily bypassed in more sophisticated attacks.
- Utilizing browser bots and valid click paths to simulate real users, thus blending in with usual traffic
- "Expanding" the botnet through free and paid proxies.
The first measure prevents the effective detection and defense against IoT bots through "invisible" browser challenges such as cookies, redirects, resource loading, or behavioral detection. Because the accesses are made by genuine browsers, that can be programmed to behave like real users, the usual Botnet-defense is rendered useless here.
The second measure ensures that there are significantly more IP addresses available for the attack than there are bots. This allows the bot traffic to be completely hidden in the data stream of normal accesses. Furthermore, it allows the evasion of geofencing-based defense measures by using proxy farms that allows to originate traffic from defined regions. Premium proxy service providers offer the ability to select between residential connections (private broadband connections), data centers, and mobile providers based on countries. Additionally, this technique enables attacks "from within" a target hosted on a cloud provider. For example, to target Microsoft Teams, one can simply rent a few nodes nearby, hoping that the protection mechanisms against their own IPs are more lax. This approach has proven successful in the case of Microsoft.
These methods are currently (2023) being utilized in more sophisticated attacks, as demonstrated by the examples above, all from June 2023.
Countermeasures
Well ... not many. and they all have flaws.
Options:
- Human-only-solvable captcha
- playing Whack-A-Mole with identifiying Proxy-Abuse and then block the IP-Ranges the proxies come from. you need. agood engineering-team and deep visibility of your dataflows to be able to indentify and distinguish proxyusage from real users
- Ratelimiting
Problems:
- Captchas: with a big enough trainingset, we solved various captchas in-browser, utilizing ML and a handfull of smart guys
- Blocking IP-Ranges: you need visibility and the ability to analyze and filter all request various firrent features (IP/Geo/AS/RPS) etc to find pattern. this will not work if the attacker utilizes proxyservices with residential ips
- Ratelimiting: this will not work if the attacker-botnet is huge, but each bot blends in with the normal traffic
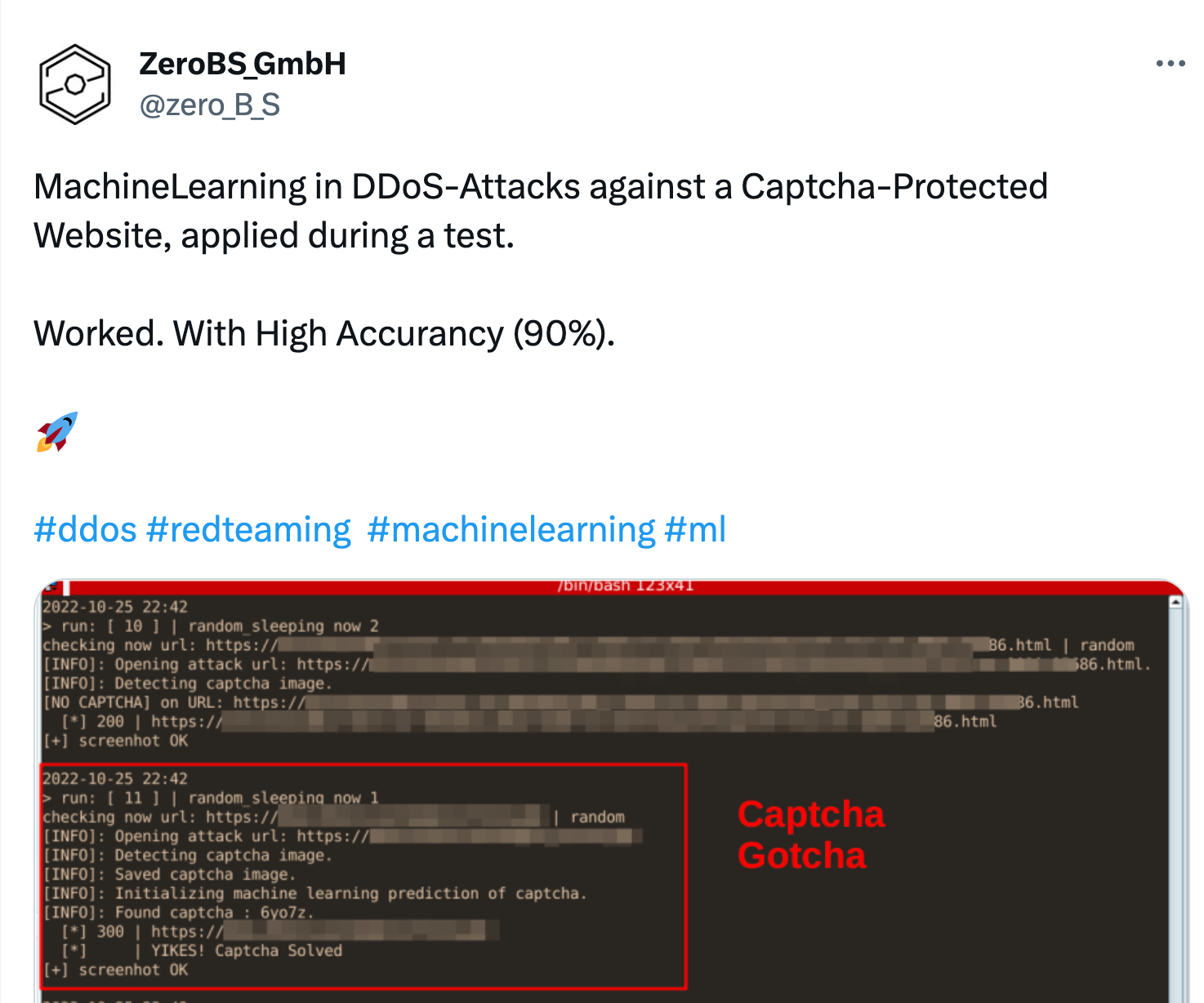
Paid Proxies
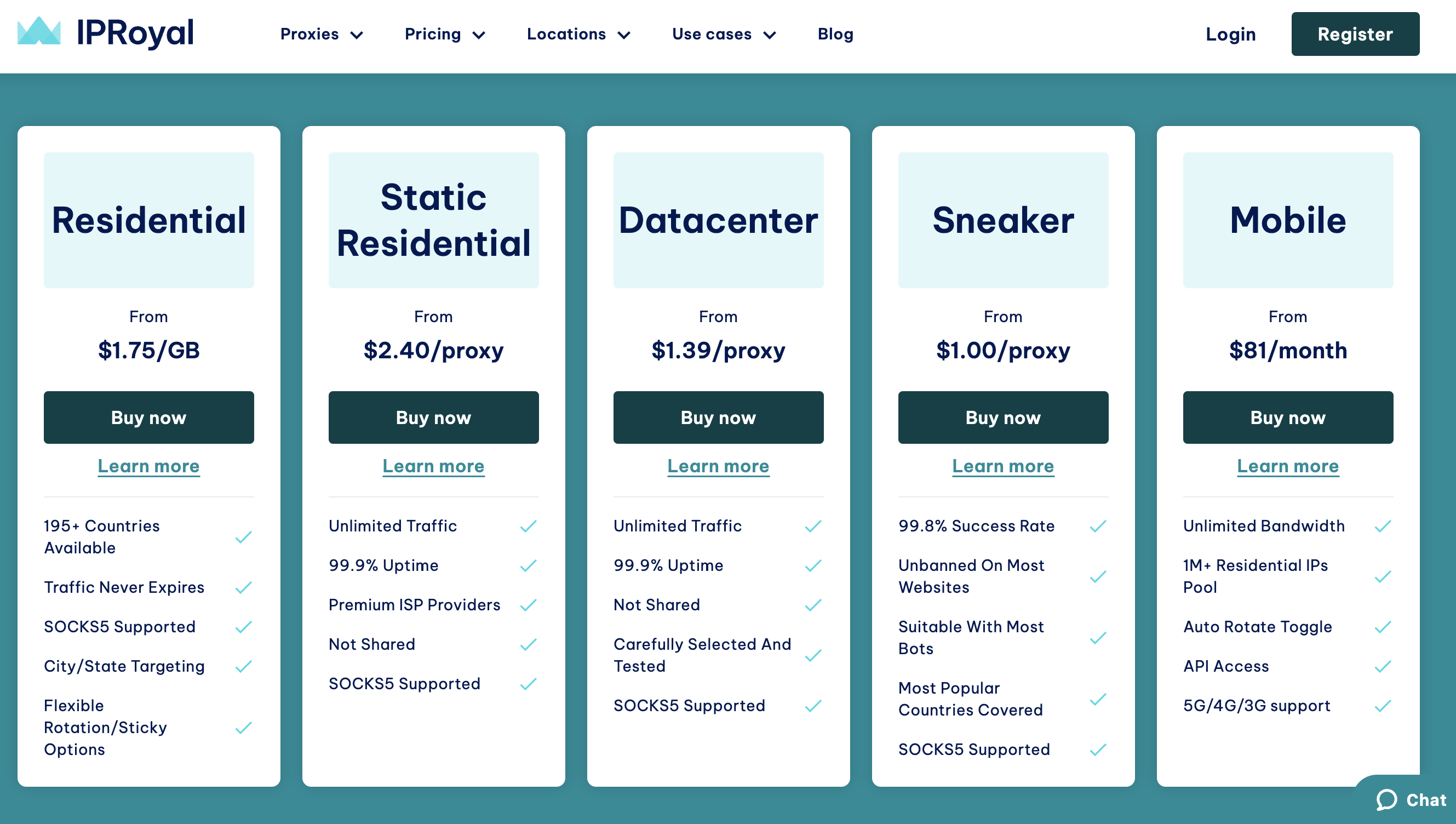
Btw, finding free proxies isnt difficult and already included in modern DDoS Frameworks. Finding Paid proxies isnt either, there is a good summary/list on techjury.
Below sample-Screenshots from a services.
Timeline
- 2023-07-01: changed status from members-only to public
- 2023-07-01: Twitter added
- 2023-06-29: Akamai added
- 2023-06-25: Microsoft added
- 2023-04-12: intial release (members only)


Member discussion: