2022 saw a handfull of interesting developments, one of those beeing the use of Open-Source Intelligence (OSINT) techniques, which advanced significantly, leading to a rise in successful attacks from DDoS attacker gangs like Killnet and Noname. These groups were able to use OSINT to gather sensitive information about their targets, such as IP addresses, network configurations, and vulnerabilities, which they used to launch devastating DDoS attacks.
From attacking only Main Websites and Company-Portals in late spring 2022 we have seen especially KillNet (and later on all Hacktivist-Groups) develop its own skillset using OSINT.
This special technique, which isn't new among IT-Security-Specialists and RedTeamers, allows adversaries to identify targets in an infrastructure that, when attacked, really can do harm, cost money or limit operational abilities. Below is a short list of attacked targets over the last 6 months that has been found and identified using OSINT:
- Login-API from Starlink
- MobilePayment-Systems of Banks
- VPN/Employee-Login-Portals form all sorts of Companies and Organisations
- B2B-Portals from Companies
- various Payment-System
- Payment/Booking-Systems of Tokia Subway
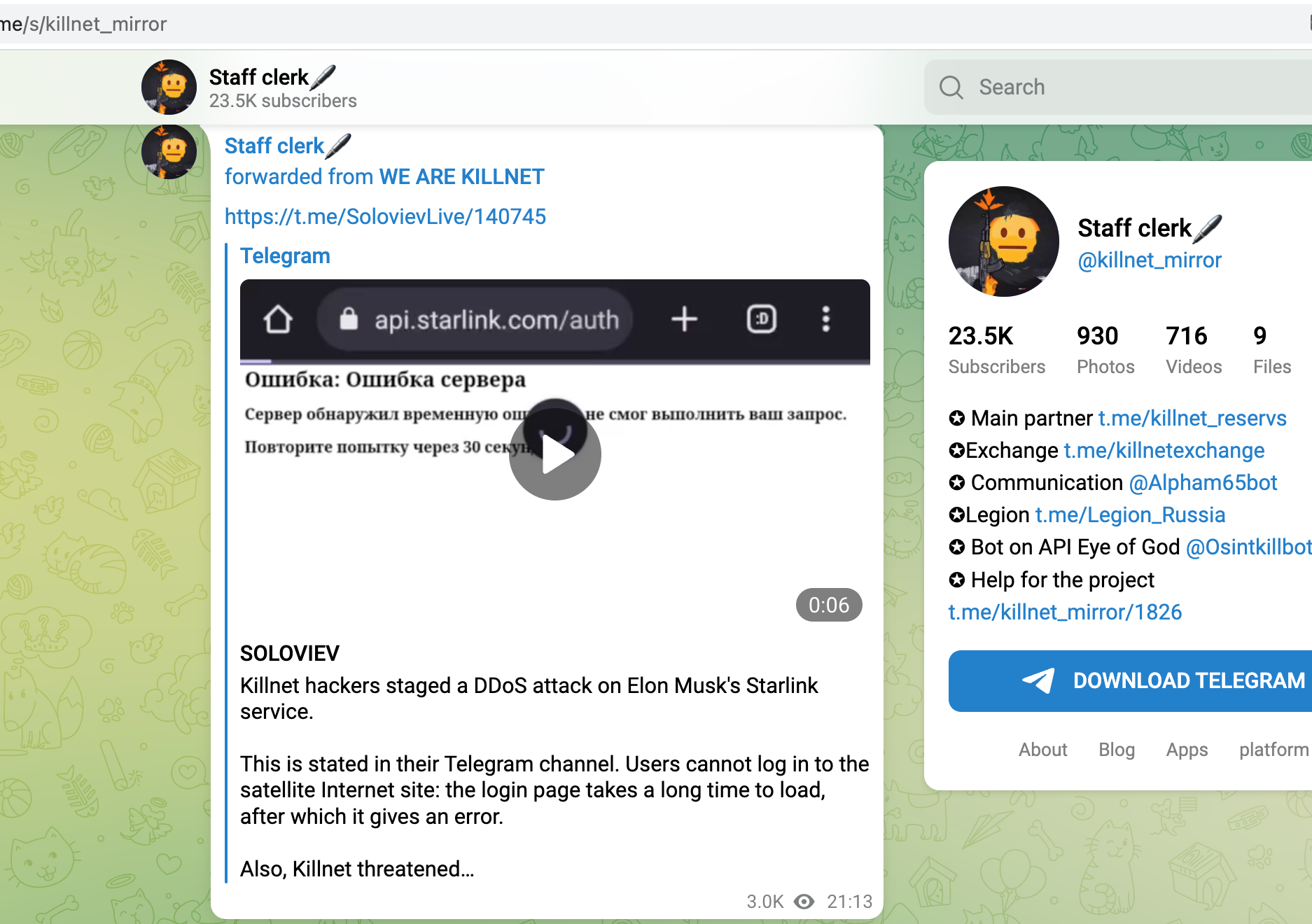
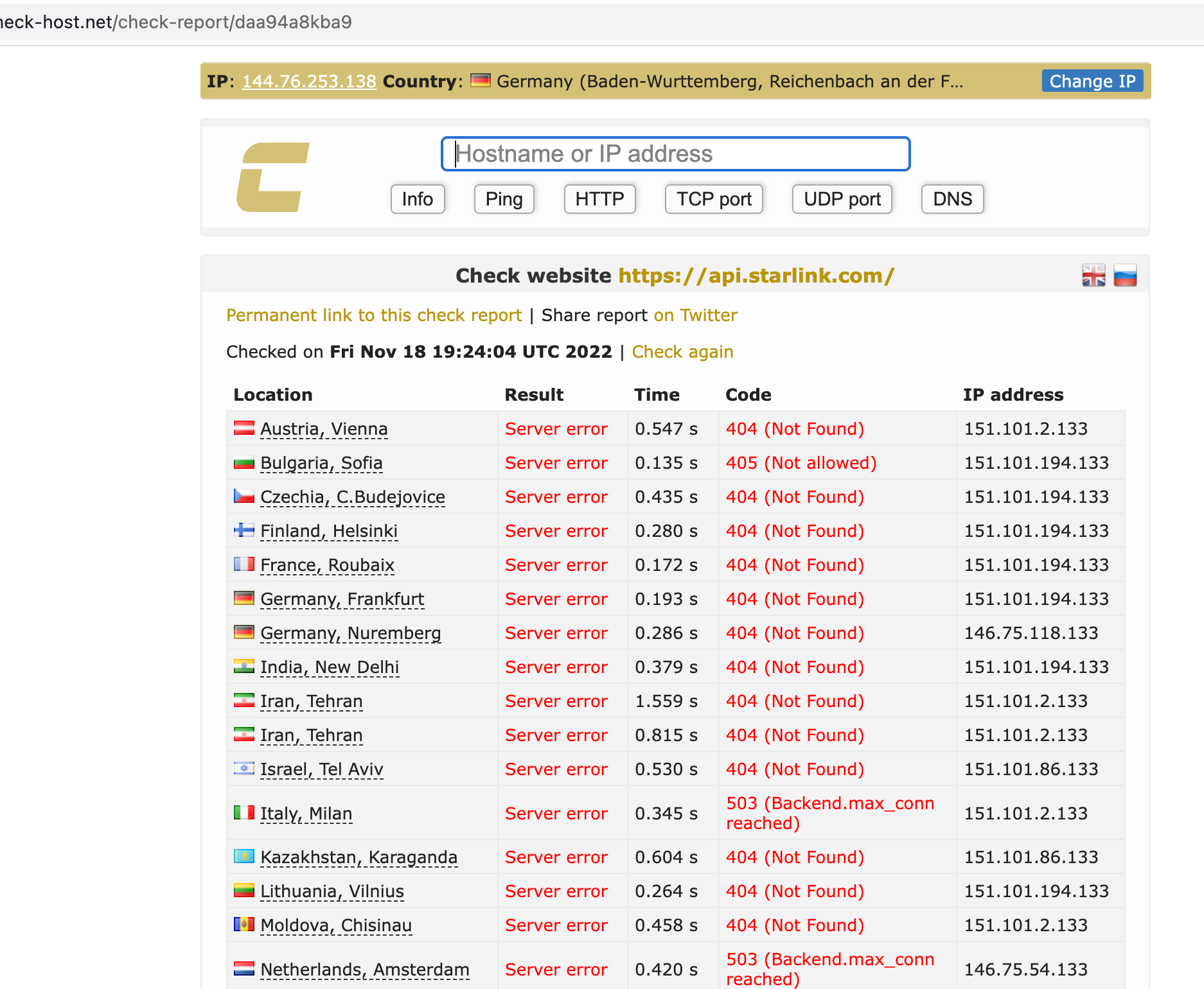
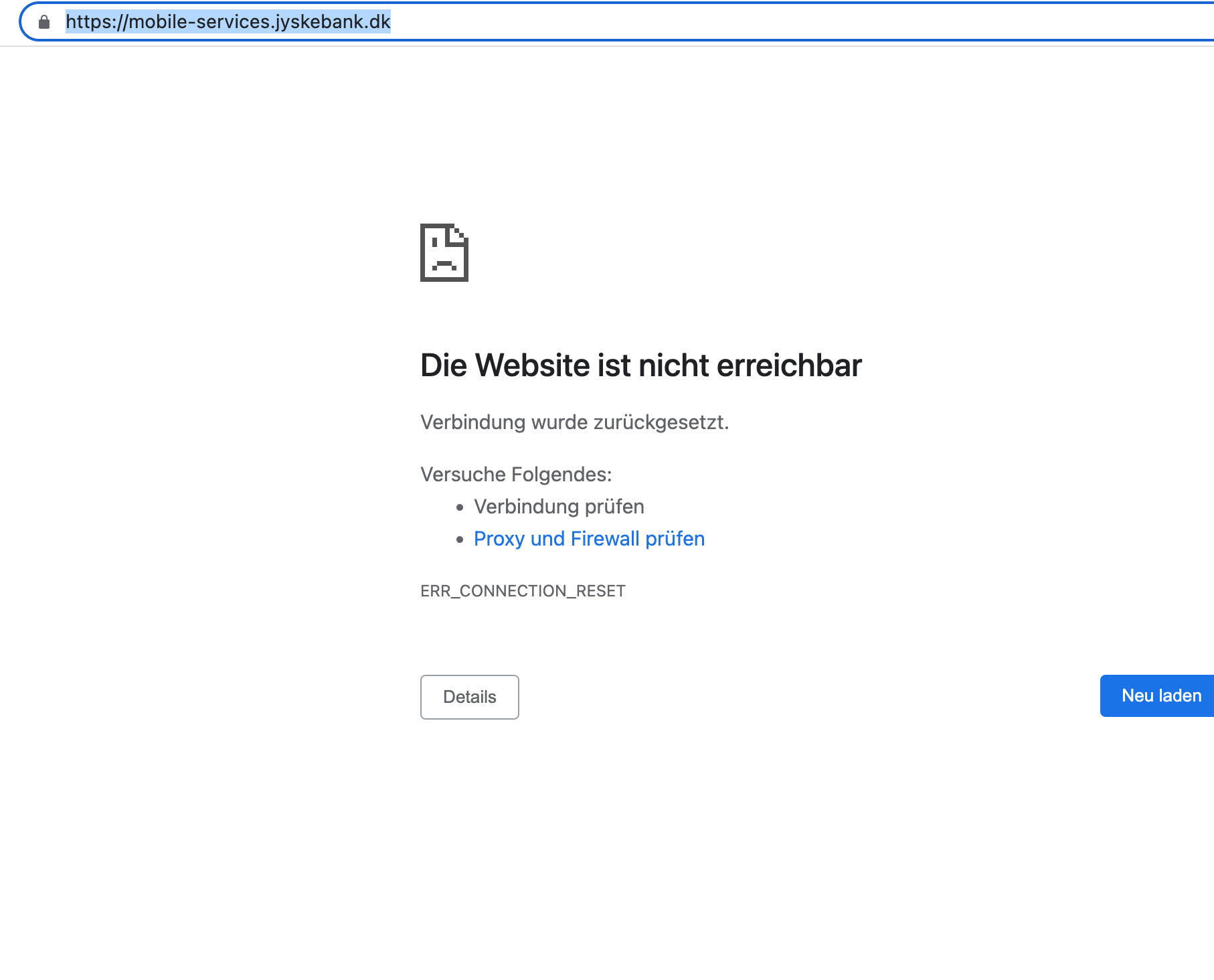

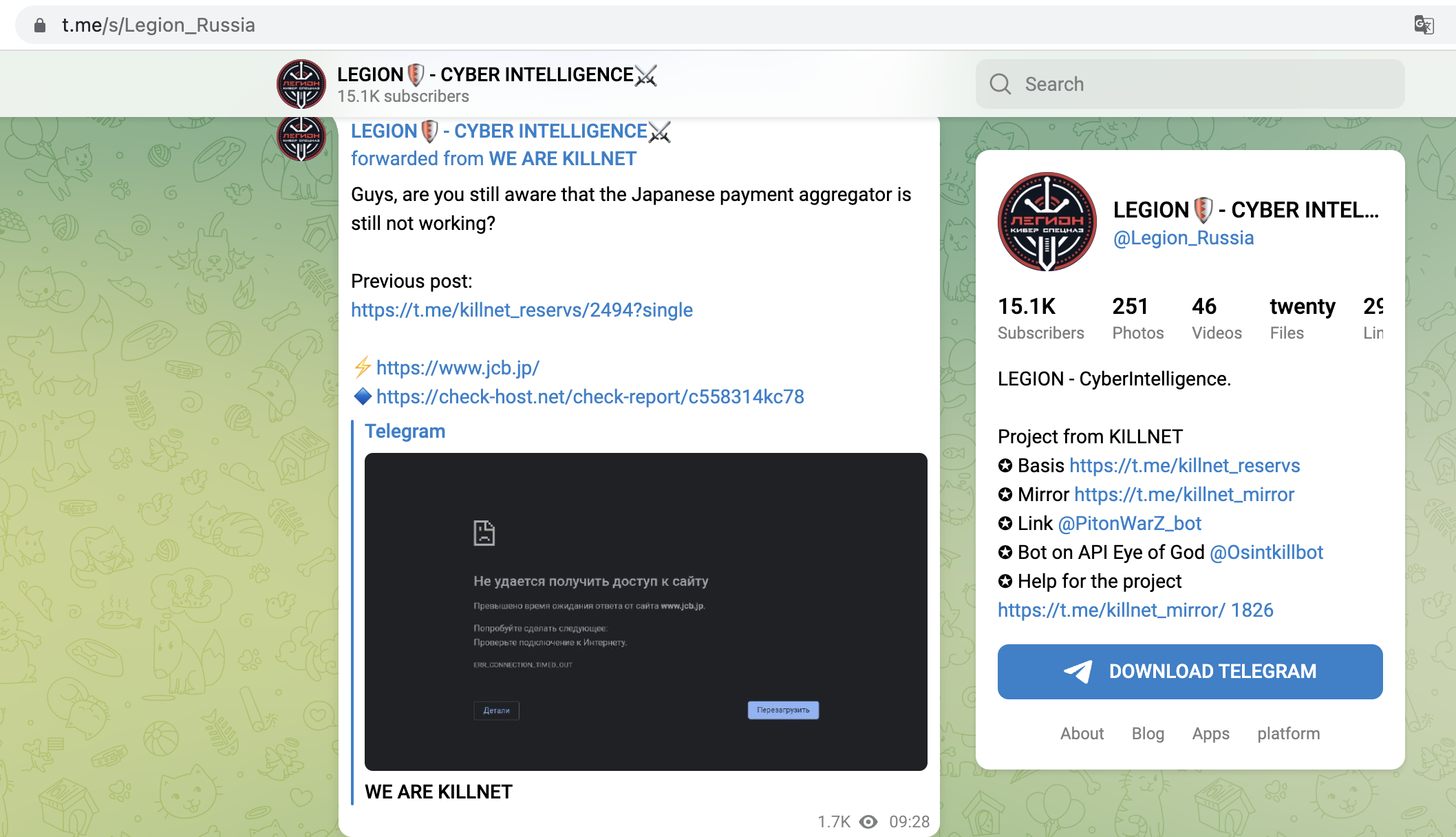
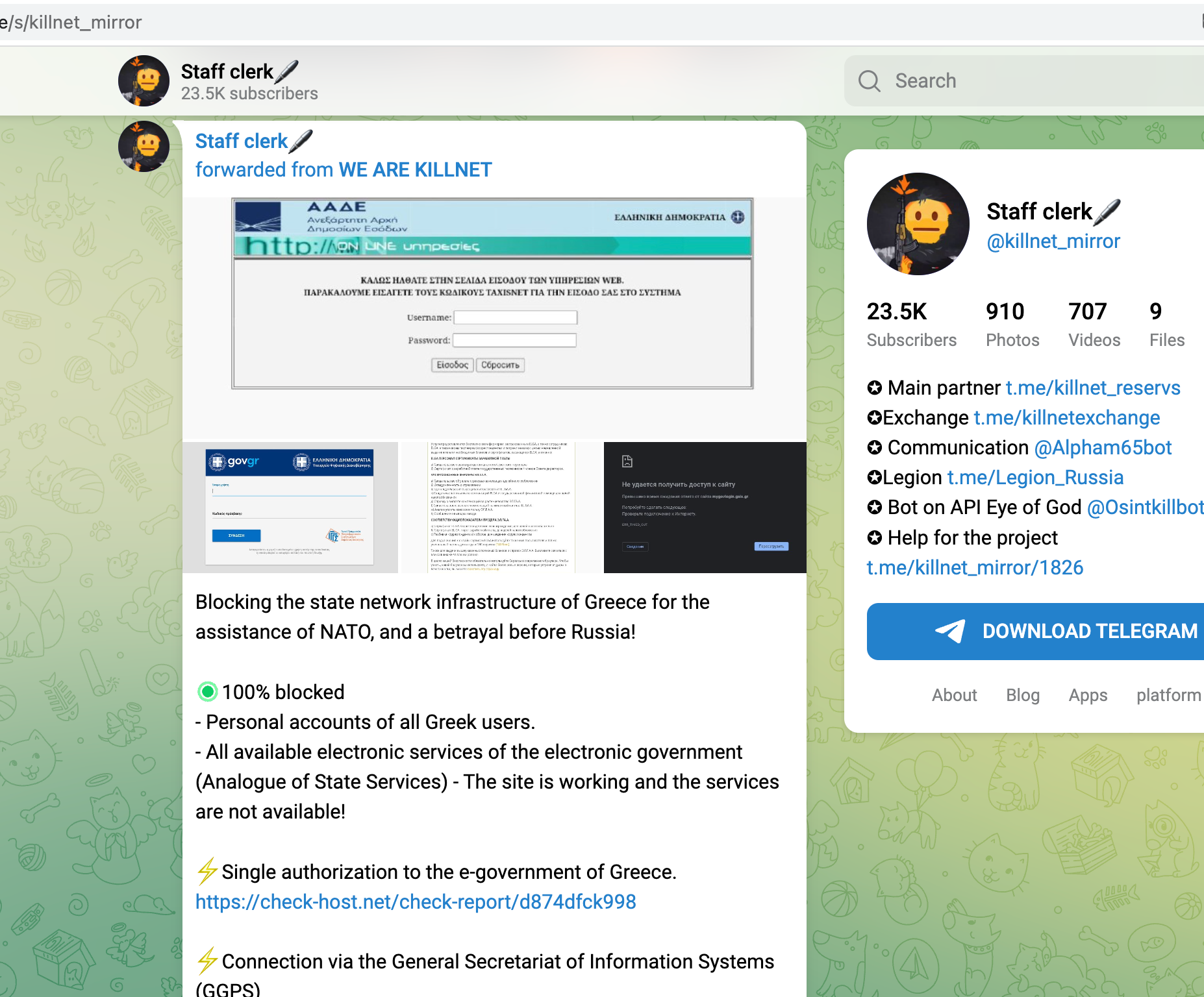


The OSINT technique used was reconnaissance. Attacker gangs would use various tools and techniques, such as port scanning and network mapping, to gather information about their targets' networks and systems. This information was then used to identify vulnerabilities and plan attacks.
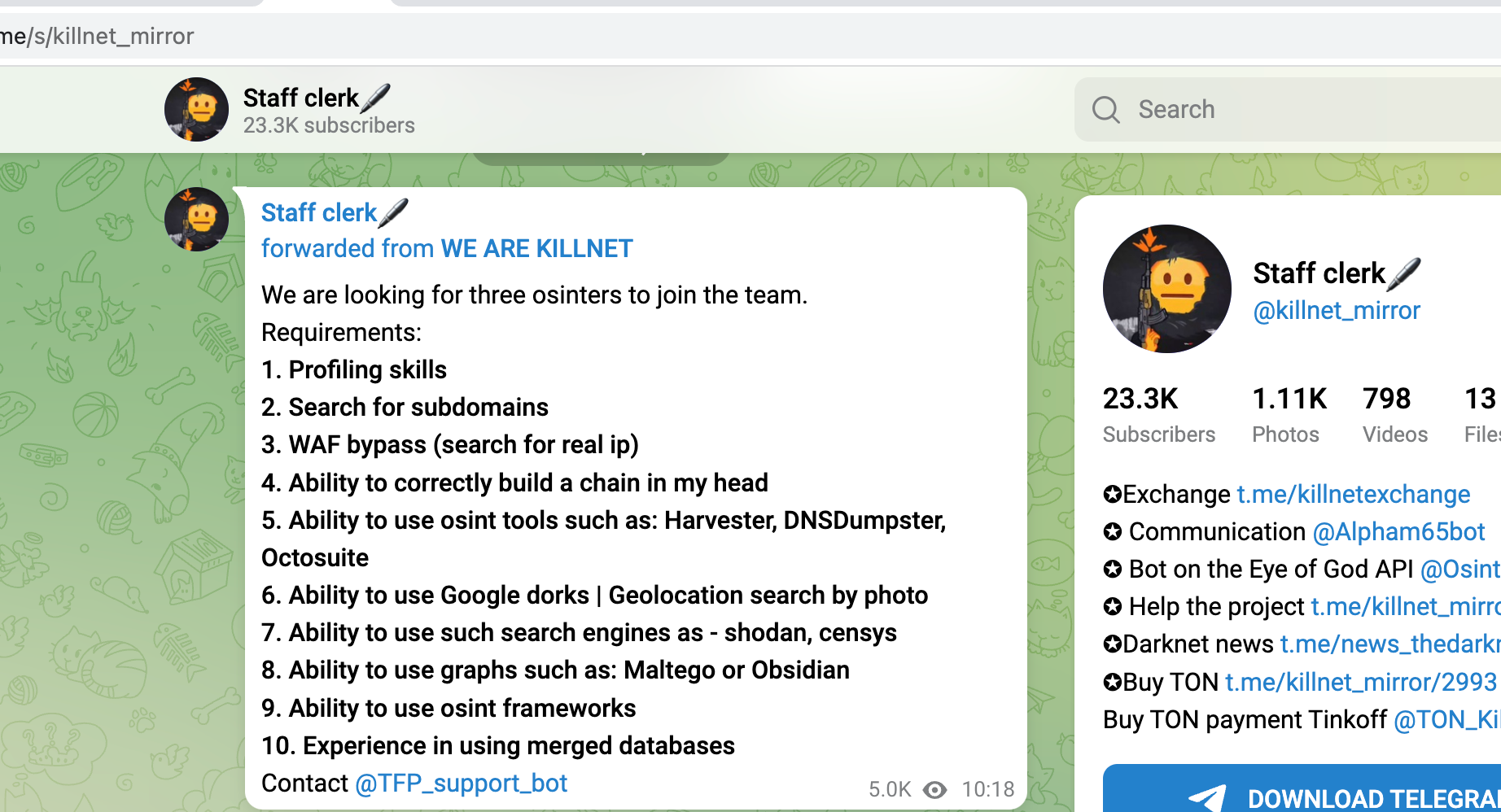
Target-Selection via OSINT and Recon is so successful, that the Killnet-Group is actively seeking new staff to help them with DDoS and hacking, as seen in a Telegram-Post from December 2022
And it's not just us, noticing that trend. Security-Specialist Netscout mentioned OSINT - methods like recon and monitoring in its 2022 Threat-Report, Chapter "Adaptive DDoS Attacks and Learning How To Suppress Them"

In conclusion, the development of OSINT techniques in 2022 was a significant factor in the success of DDoS attacker gangs like Killnet and Noname.
These groups were able to use reconnaissance techniques to gather the information they needed to launch devastating DDoS attacks.

Member discussion: