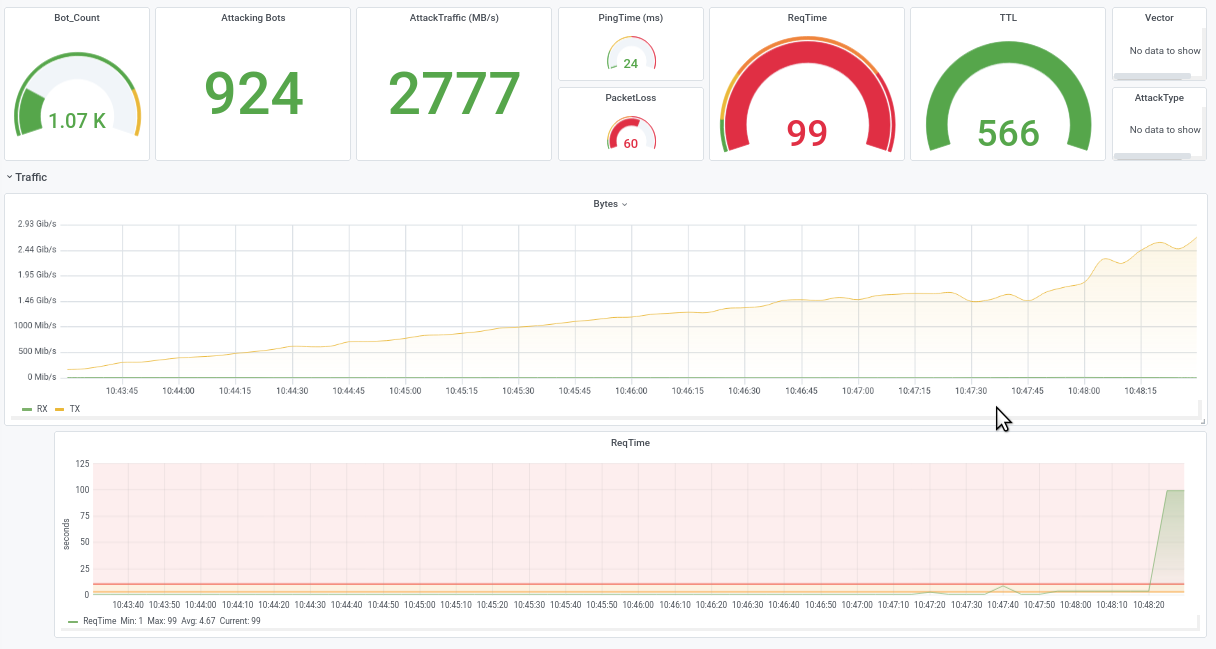
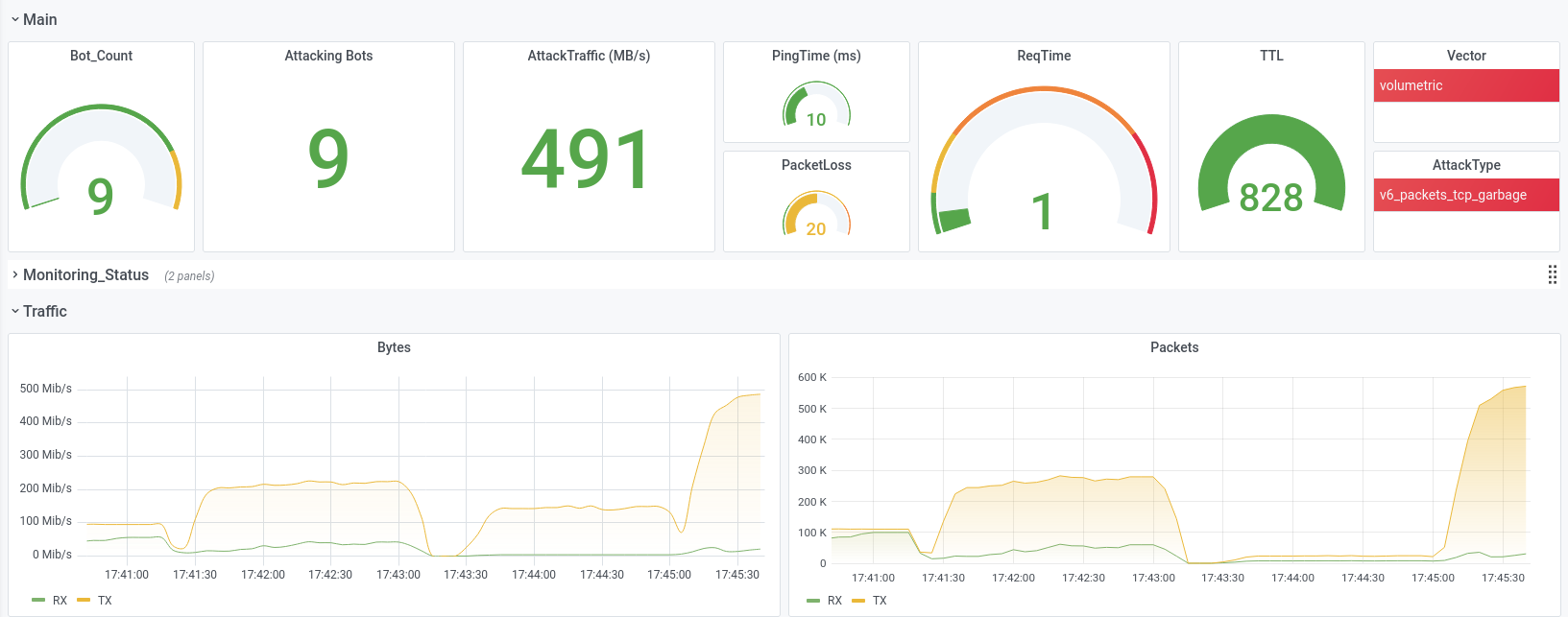
Since early 2020 we are testing DDoS-Stresstest for IPv6 - targets with both "classical" attacks like UDP/TCP-floods, but also leveraging IPv6-specific attackvectors, without diving too deep into the protocol already, leaving room for a steep learningcurve that we are willing to climb.

currently available IPv6-DDoS-Tests src
There is this excellent presentation from Airbus/EADS Corporate Research Center that has some good hints about possible attackvectors (Packet/RouterPingPong FTW), but there is also a well established IPv6-Attack-Framework from TheHackersChoice thc-ipv6 that is a treasure-trove of nice inspirations on that topic.
In 2021 we have seen an increase in attacker-sophistication, with direct TCP-Attacks, Recon and new vectors, leading to more innovation in this sector; we have seen more skalpel-like clean attacks and not so many rusty swords or sledgehammers.

from the latest Netscout Threat Intel-Report 2021/2H, src
With increasing sophistication, we expect also more IPv6-based DDoS-attacks in the near future, because we learned of the last 12 months with our partners and clients, that IPv6 is a very effective attackvector.
Furthermore, certain protection-providers completely neglect IPv6, while others asked us not to test IPv6 "so intense, or maybe later in 2022"
Our Experiences so far from a dozen IPv6-tests:
Member discussion: