[ Disclaimer: written withouth the help of AI/LLM]
SlowLoris, although developed in 2009 by RSnake and thus an old DOS technique, found its way into modern attack tools, and is used especially by larger botnets. We will explain in this article, why SlowLoris-attacks are an issue again.
SlowLoris in a nutshell: during the attack, an extremely large number of HTTP connections are opened, but never completed. For more details, sourccode and background on the SlowLoris-Attack, see the links in the references below.
While SlowLoris was a very successful attack technique 10-14 years ago, due to the dominance of the Apache web server at the time (nginx, for example, was never vulnerable to it), the issue itself was actually fixed around 2015. Fast Forward 2022: Infrastructures have evolved massively, the webstacks have grown enormously in size and complexity: DDoS appliances, firewalls, loadbalancers, TLS offloaders, even more loadbalancers, CloudStacks, MultiCloud, Orchestration, serverless, autoscaling, APIs, OAuth, SingleSignOn, etc. The web is now Layers Ontop of Layers Ontop of Layers.
This is where the "modern" Slowloris attacks come in. The original Slowloris was launched from a single computer and was successful even through tor, but was meant to attack a single webserver.
Modern DDoS botnets have 1000/2000/5000 or more bots, often servers, all launching a Slowloris attack at the same time, and can thus open and keep open millions of HTTP connections. The result: one of the interconnected components can no longer open new sessions, and the DDoS-attack is thus successful.
And since protocol-attacks/stack-attacks became widespread in 2022, we deliver more and more SlowLoris-attacks during Layer-7-DDoS-Stresstests, mostly upon requests by clients, with a 50% success-rate.
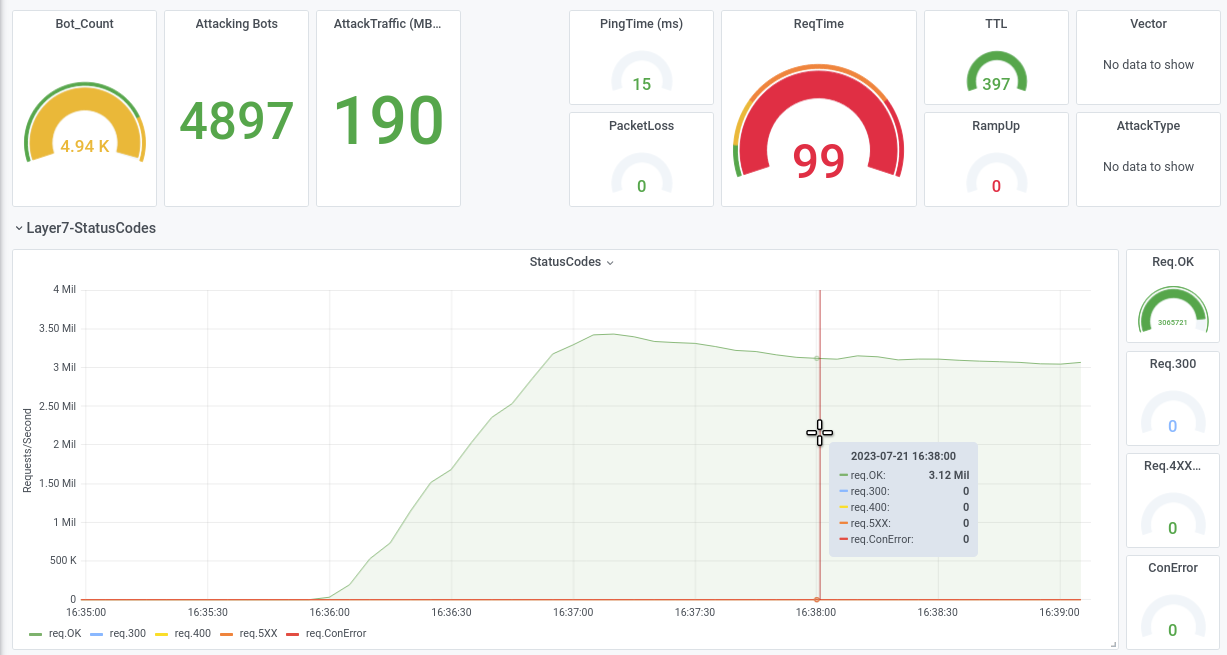
The first screenshot was taken during a test with 5000 bots against a well-sized loadbalancer-cluster and shows the effects quite well. The bots keep almost 3 million HTTP connections open, no new requests can get through, and the DDoS attack is successful.
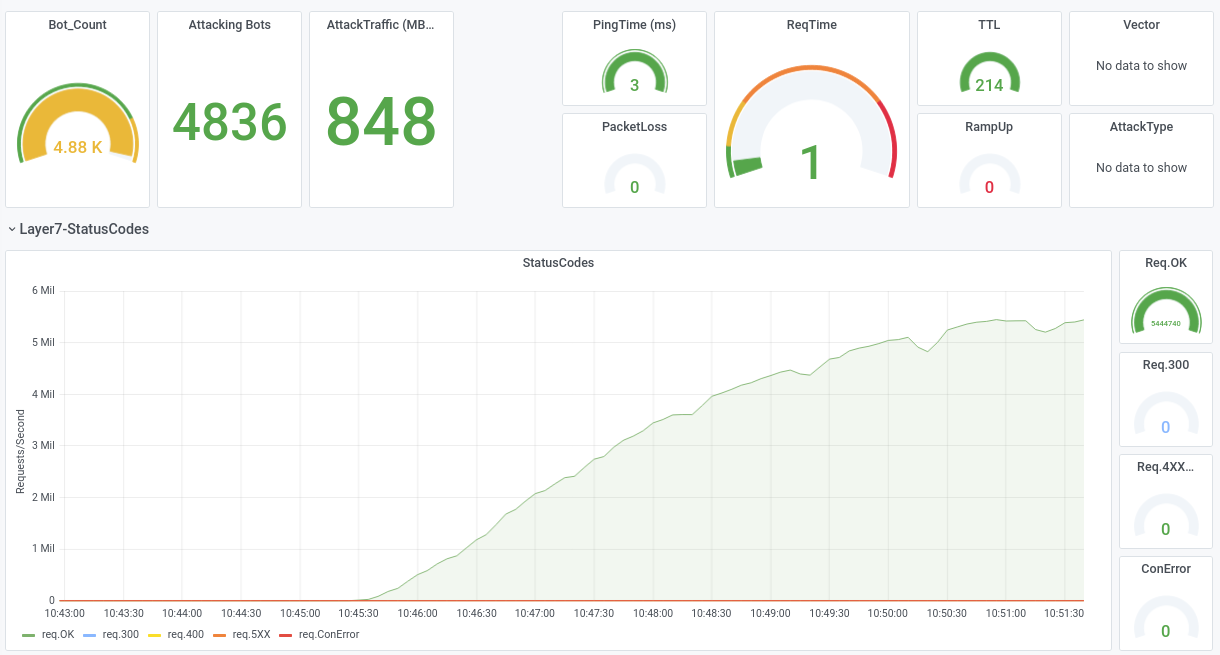
The next screenshot shows the same attack against Cloudflare, which is completely unimpressed despite 5 million open HTTP sessions.
The "charming" thing about Slowloris from the attacker's point of view: the attack is not so easy and obvious to detect and mitigate, because
- In contrast to a normal GetFlood, the HTTP requests are not completed and are only renewed sporadically.
- Therefore, the normal WAF/BotDefense does not see a continuous fire and cannot block.
- The traffic does not increase significantly overall, and since new connections are not initiated continuously, various rate-limiting modules or SynFlood detection are "blind". The only indications are the running TCP sessions on firewalls and HTTP sessions on load balancers.
The problem is so immanent that even Microsoft and the Azure cloud had problems with a massive Slowloris attack in June 2023.

And as always, if one attack vector is successful and makes it into the media, all the other actors will follow suit. So we will see more SlowLoris in the next months, since Layer-7-Attacks are "THE THING" in 2023 anyway.
Happy fragging.
References
- WriteUp with technical Details https://github.com/StanGirard/SlowLoris-DDOS-Attack
- Github-Repo with the original Scripts https://github.com/XCHADXFAQ77X/SLOWLORIS
- Wikipedia on Slowloris https://en.wikipedia.org/wiki/Slowloris_(computer_security)
- Cloudflare on Slowloris https://www.cloudflare.com/en-gb/learning/ddos/ddos-attack-tools/slowloris/
- Microsoft admit beeing a victim of a massive slowloris-attack https://msrc.microsoft.com/blog/2023/06/microsoft-response-to-layer-7-distributed-denial-of-service-ddos-attacks/

Member discussion: