Recently Cloudflare, Google and Amazon published information on a DDoS-Zero-Day that has been seen in the wild since summer and that leads to immense attackrates. It goes by the Name "HTTP/2 RapidReset" and has even a CVE attached, CVE-2023-44487.
If you havent heard of this attackmode, you will find all details in the linklist below, but a short TL;DR:
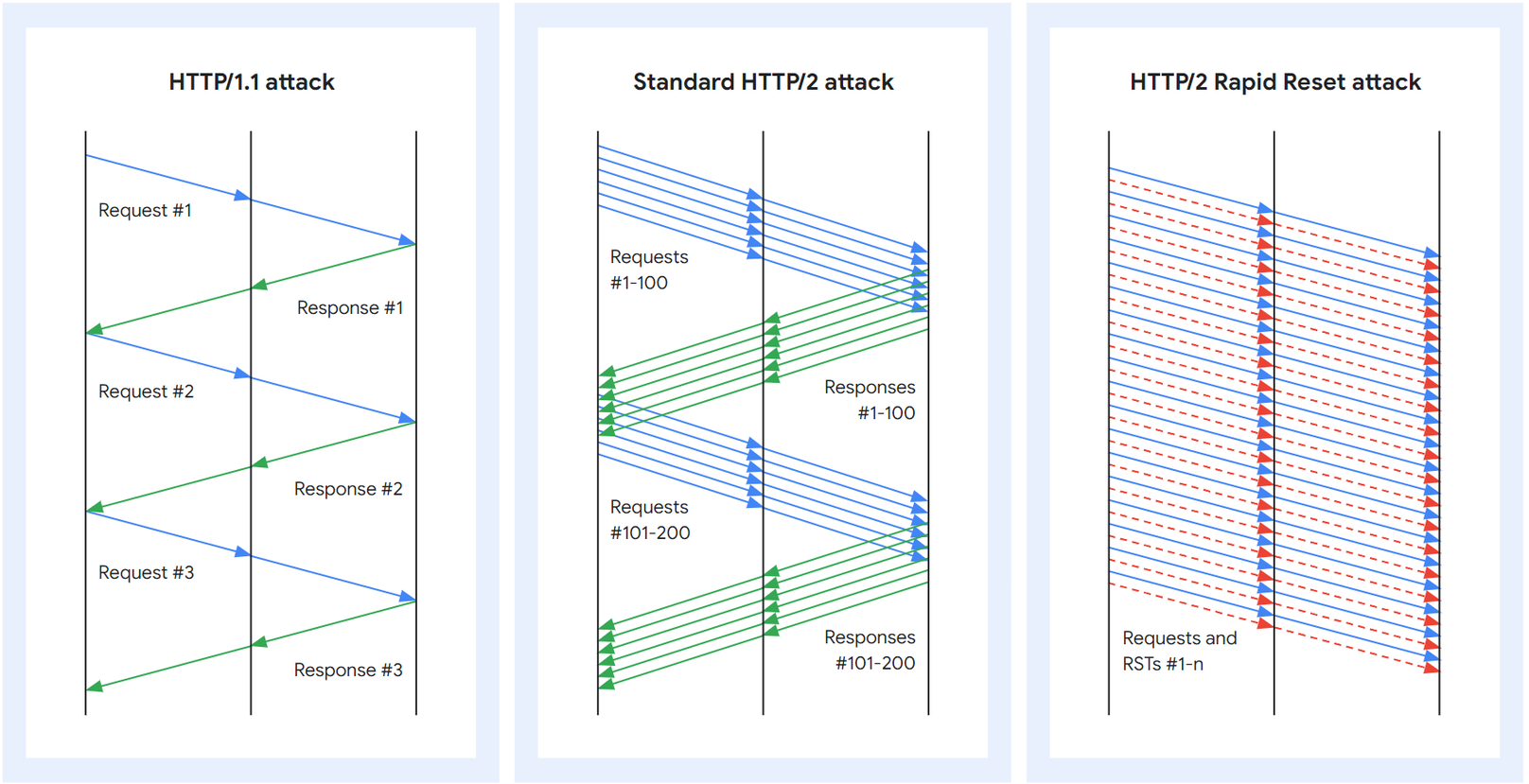
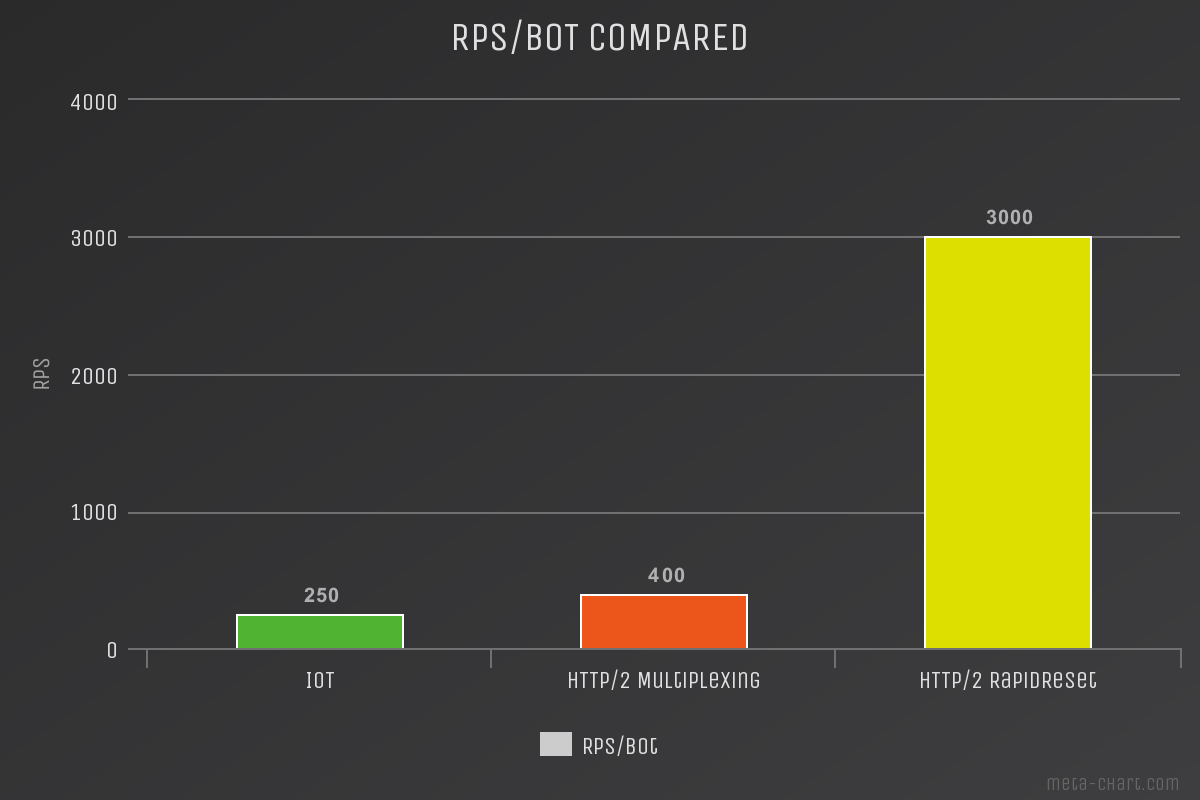
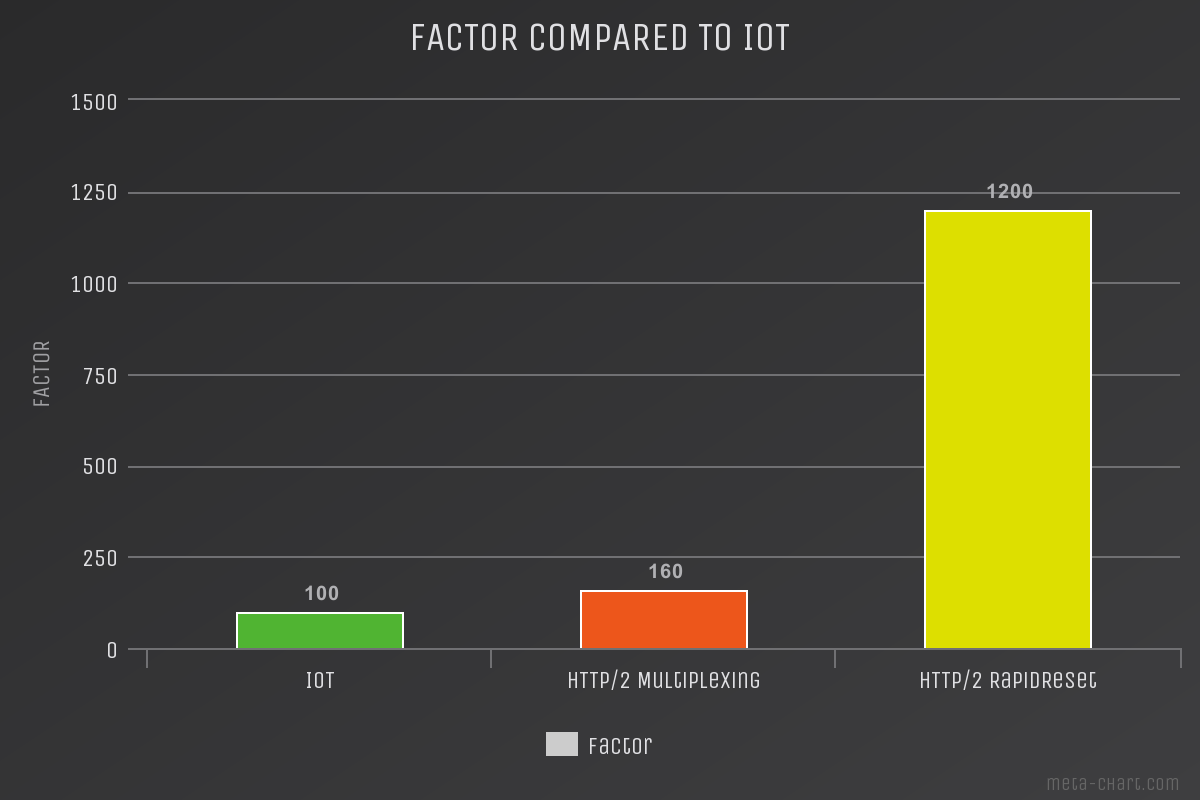
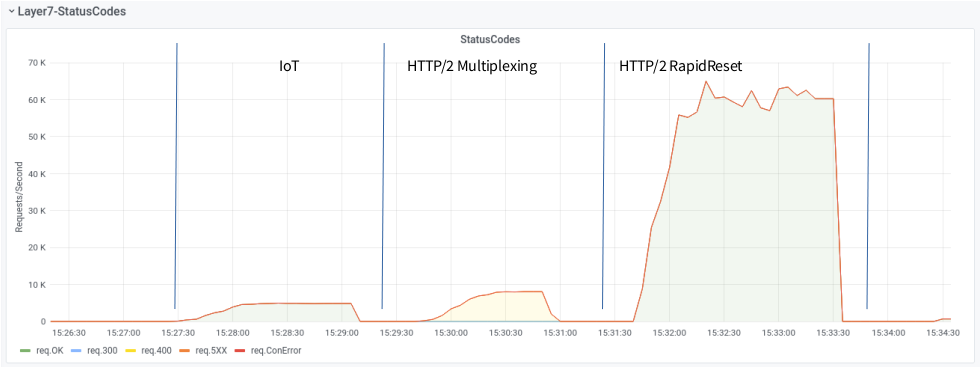
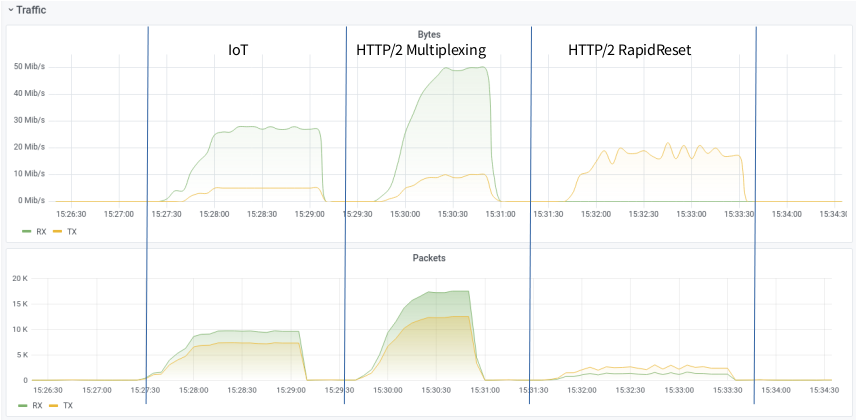
We measured the attack-potential of the new RapidReset-Attack vs established vectors and compared it to the Firepower (RPS, Requests/Second) of IoT - Bots. We used a small Botnet and our well beloved target, aka zeroBS Webserver. Ordered attackrate, threads etc has always been the same. As you can see in the charts below, the attackrate of HTTP/2 RapidReset is remarkable higher that HTTP/2 Multiplexing.
What is also notable: the Trafficpattern differs totally between HTTP/2 Multiplexing and HTTP/2 RapidReset.
References on HTTP/2 RapidReset, CVE-2023-4448
Advisories
- https://cloud.google.com/blog/products/identity-security/how-it-works-the-novel-http2-rapid-reset-ddos-attack
- https://blog.cloudflare.com/zero-day-rapid-reset-http2-record-breaking-ddos-attack/
- https://www.f5.com/company/blog/http-2-rapid-reset-attack-impacting-f5-nginx-products
- https://www.netscout.com/blog/asert/http2-rapid-reset-application-layer-ddos-attacks-targeting
POCs
Alerts
Technical breakdown
- https://twitter.com/dcuthbert/status/1712026660608827888
- https://blog.cloudflare.com/technical-breakdown-http2-rapid-reset-ddos-attack/
Affected
- NIST https://nvd.nist.gov/vuln/detail/CVE-2023-44487
- Google, Amazon and Cloudflare, any SaaS-Privider
- Nginx / F5 https://twitter.com/nginx/status/1711727100892168635

Member discussion: