Intro
In early April 2024, Bartek Nowotarski disclosed a new DDoS attack technique named "HTTP/2 Continuation Flood", which exploits vulnerabilities in various HTTP/2 implementations.
the tl;dr from his advisory:
The CONTINUATION Flood is a class of vulnerabilities within numerous HTTP/2 protocol implementations. In many cases, it poses a more severe threat compared to the Rapid Reset: a single machine (and in certain instances, a mere single TCP connection or a handful of frames) has the potential to disrupt server availability, with consequences ranging from server crashes to substantial performance degradation. Remarkably, requests that constitute an attack are not visible in HTTP access logs.We've examined and reconstructed the vector, and can confirm its effectiveness against several systems tested. In addition to the list below, we've also identified popular hardware Loadbalancers as vulnerable; we are currently clarifying whether this is a general or specific issue.
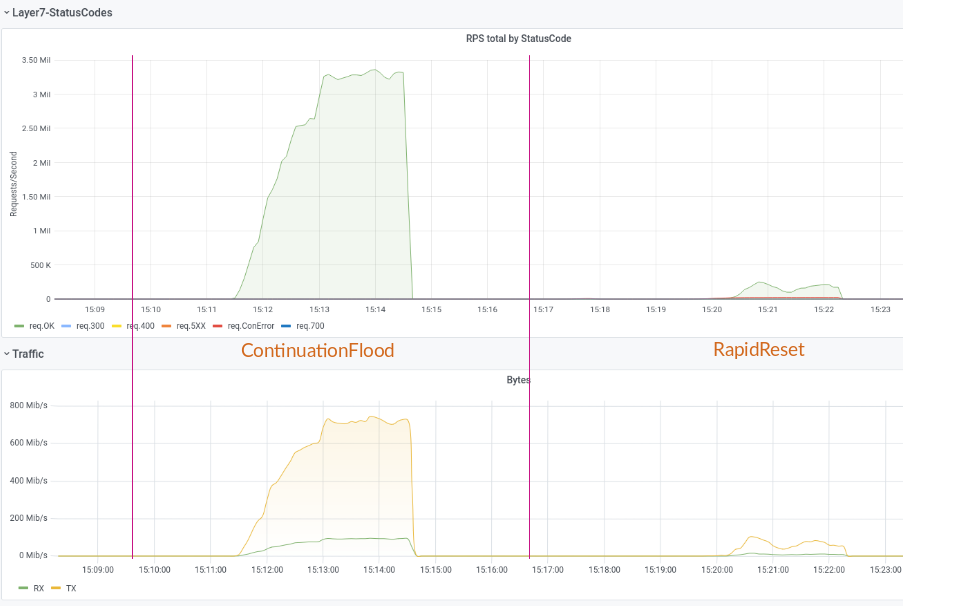
One of the best "features" of the new attackvector: no log entries, because similar to Slowloris, requests are never completed.
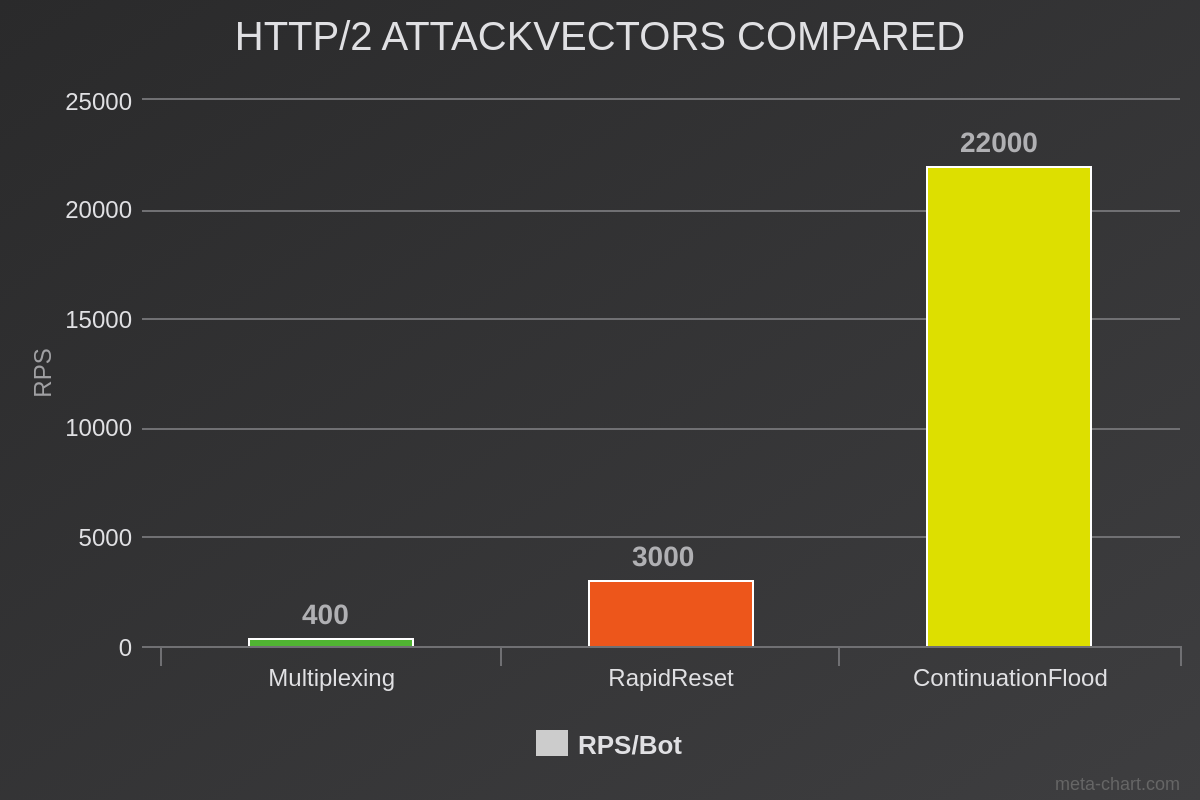
When we compare ContinuationFlood with RapidReset, the true potential comes to light: while RapidReset was almost 8 times as powerful compared to normal HTTP/2 Multiplexing attacks, ContinuationFlood is 7 times stronger than RapidReset in terms of pure Requests per Second (RPS) per bot.
According to Bartek, the following projects and products with HTTP/2 implementations are affected:
- amphp/http
- Apache HTTP Server (httpd)
- Apache Tomcat
- Apache Traffic Server
- Envoy proxy (oghttp)
- Envoy proxy (nghttp2)
- Golang
h2Rust crate- nghttp2
- Node.js
- Tempesta FW
- xxxx
not affected:
Happy Testing!

Member discussion: