cool things first, explanation below
IoT-Bots
IoT-Bots are devices connected to the internet of things (IoT), typically routers, webcams, that have been infected by malware (specifically IoT botnet malware) and have fallen into the control of malicious actors.
IoT - Bots became widely known with the famous Mirai - Attacks in 2016, but are still around with botnets like Meris.
IoT - Bots are very limited in both capabilities and firepower per bot, but generate their impact through sheer size, often in the 10s of thousands. The original Mirai-Boitnet is known to have at least 65.000 Bots, and Meris nowadays counts 50.000 Bots.
Btw, the IEEE published a great article on the history and background of Mirai: The Strange Story of the Teens Behind the Mirai Botnet
Pseudo-Browsers
Bots we define as Pseudo-Browsers are able to mimic browser-behavior to a certain extend: they can
- follow redirects
- keep a session-store
- execute logins
- solve javascript-challenges in-code (for cloudflare, not that simple anymore but still possible)
- can execute new HTTP/2 - attacks like RST_STREAM or Multiplexing
Pseudobrowsers are programmed with pythons requests-library/httpx-library or with Golangs http-client. The infamious DDoSia-Bot by NoName057 was initially written in Python and is now written in Golang.
The advantage of these Bots over IoT-Bots: they can pretend a little more user-like behavior and interaction, but you can still identify them easily, because Pseudobots like IoT-Bots never load additional ressources like Javascript/Images/CSS that are mebedded in HTML-Code. And they can execute HTTP/2 attacks
But that disadvantage might be eliminiated with the uprising of API-Attacks.
Browsers
Browser-Bots are fully featured headless browsers that are remote-controlled by frameworks like Selenium. While you cannot run a Browser on an IoT-Device, you can on an exploited server, and with the uprising of serverbotnets and attacks utilizing cloudservices and proxies, browserbots are the current hot thing.
There are a couple of things why attackers use Browserbots
- traditional/challenge-based Bot-Detection/Defense doesnt work so well
- with enough bots you can mimic real user-beahvior and clickpaths, bleding in the bot-traffic with normal user traffic, thus making it harder
- HALO-Attack/Upstream Jamming is easy going with browserbots
- you can easily implement ML to solve simple captchas
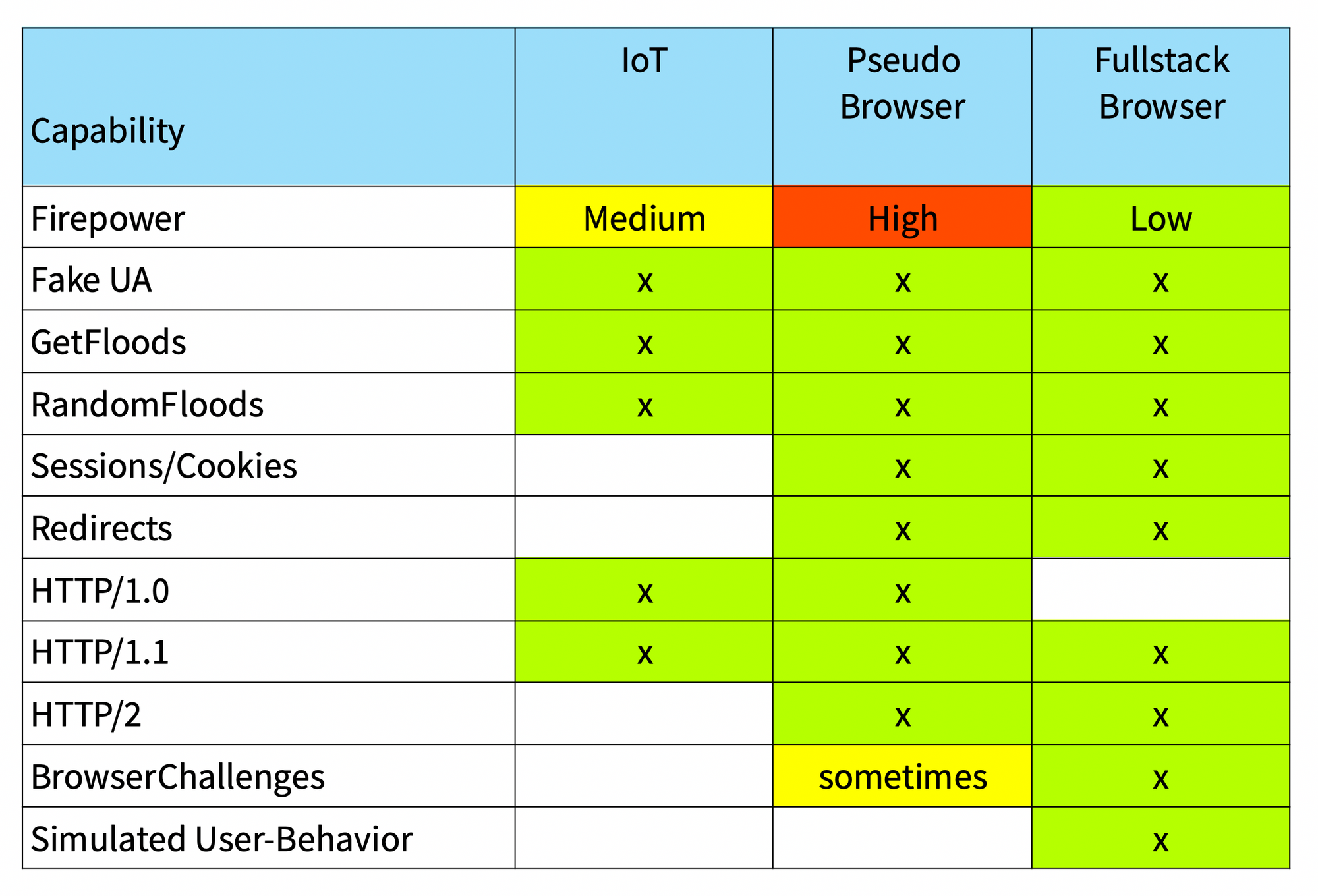
Comparison

- Firepower: means Requests per Seconds, RPS. IoT is between 5-10 RPS, Pseudobrowsers up to 200 RPS, Browsers 1-5 RPS, all measured against an HTTPS-Target
- Fake-UA: ability to manipulate the UserAgent-String in Request-Headers
- Get/Random-Floods: standard attack-menanisms of Layer-7-Attacks
- Session/Cookies/Redirects: ability to store cookies, follow redirects and simulate a full session
- HTTP/1/1.1/2.0: ability to use different HTTP-Versions
- BrowserChallenges: ability to solve Browserchallenges as Bot-Defense
- Simulated User-Behavior: ability to fully blend in as a normal user

Member discussion: