While over 100 hacktivism/groups are engaged in DDoS-attacks all over the globe, many blueteams adopt different protection-mechanism that makes it harder for DDoS-attacks to succeed, one of them beeing GeoIP-Blocks. We have seen this method beeing adopted widely and successfully in the first half of 2023.
Earlier this year we already wrote a blogpost about botnet/developments in 2022, mainly a shift towards DirectPath/TCP/Stack-attacks and the usage of browserbots in DDoS-frameworks and booterservice.
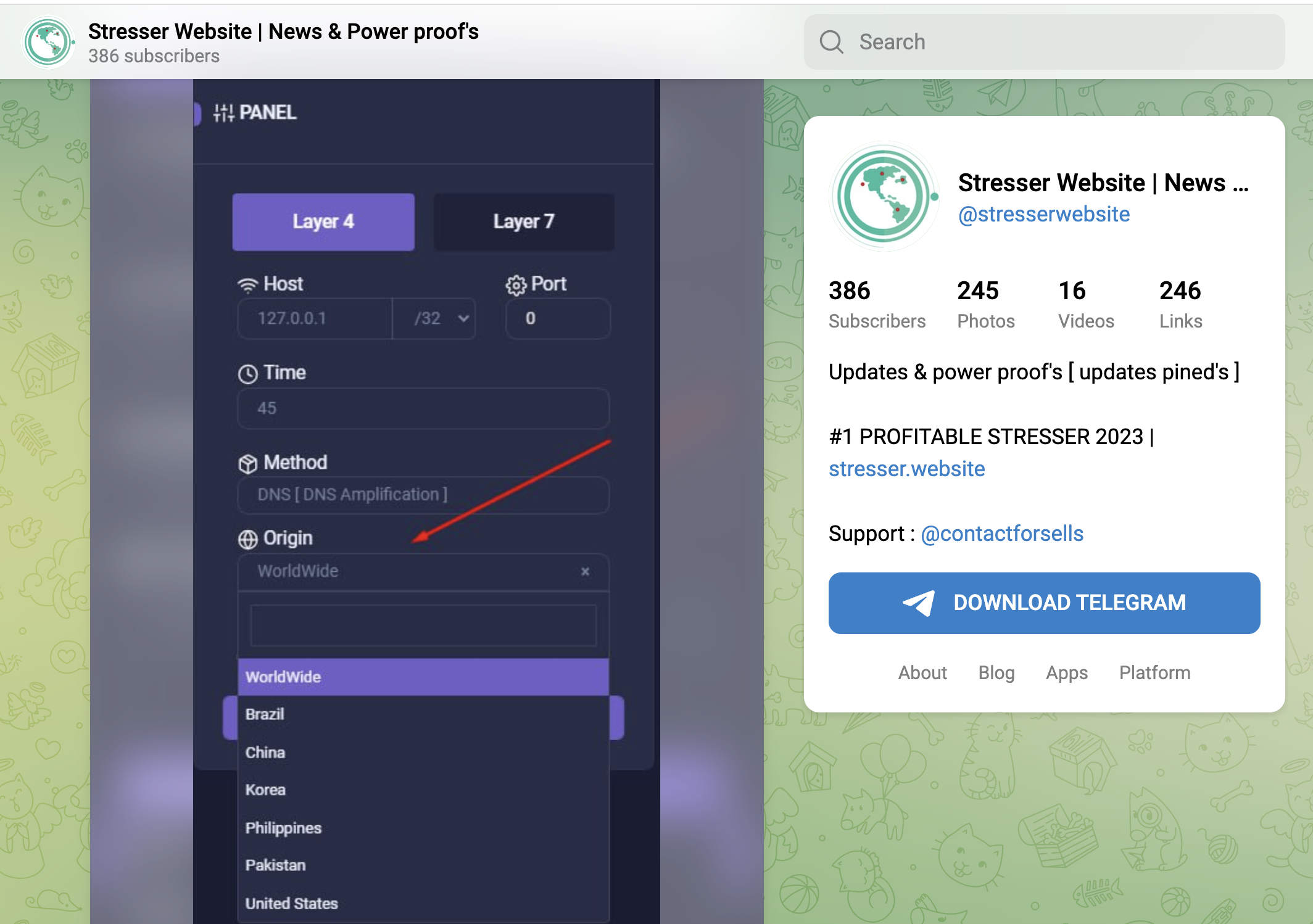
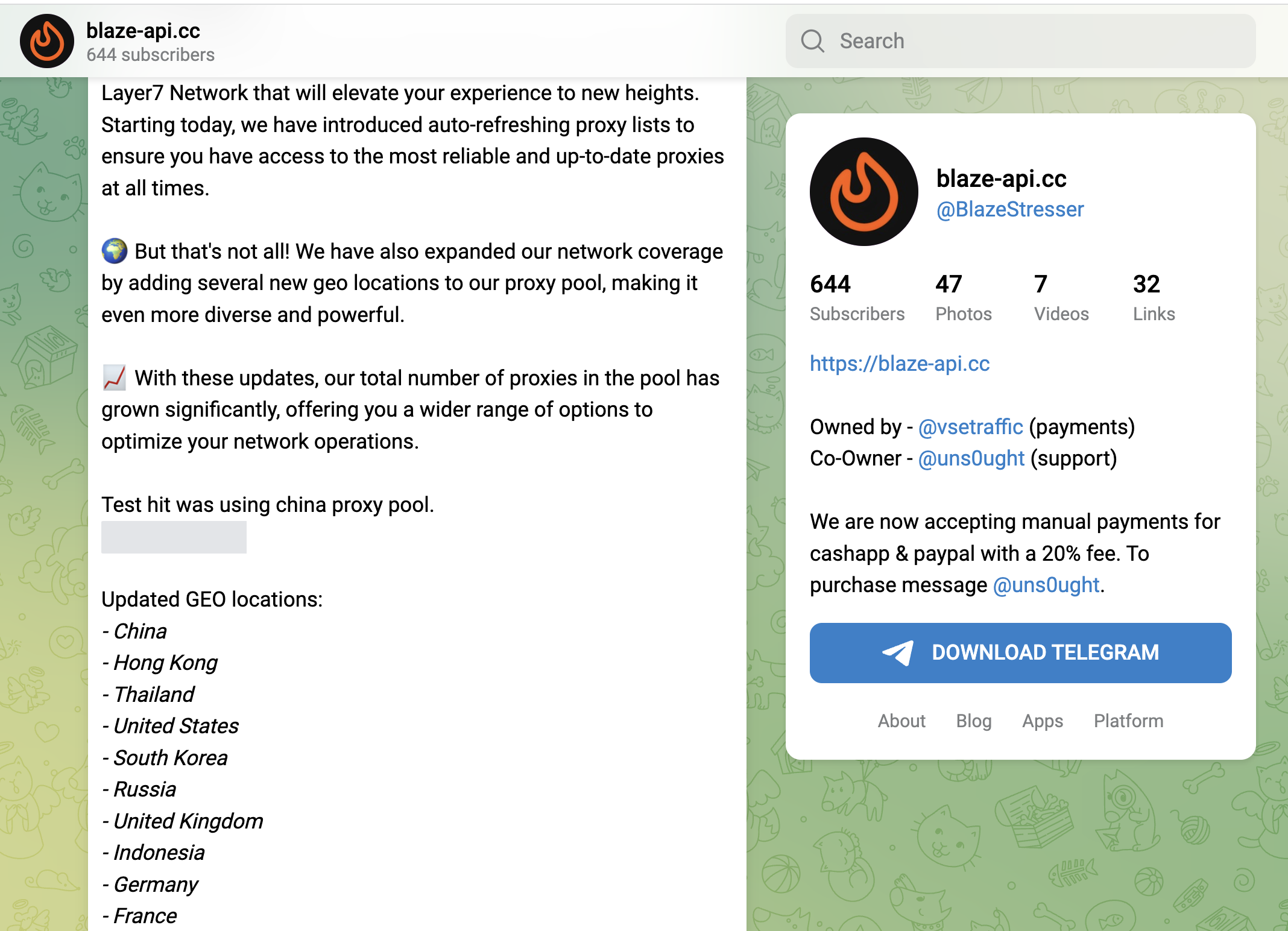
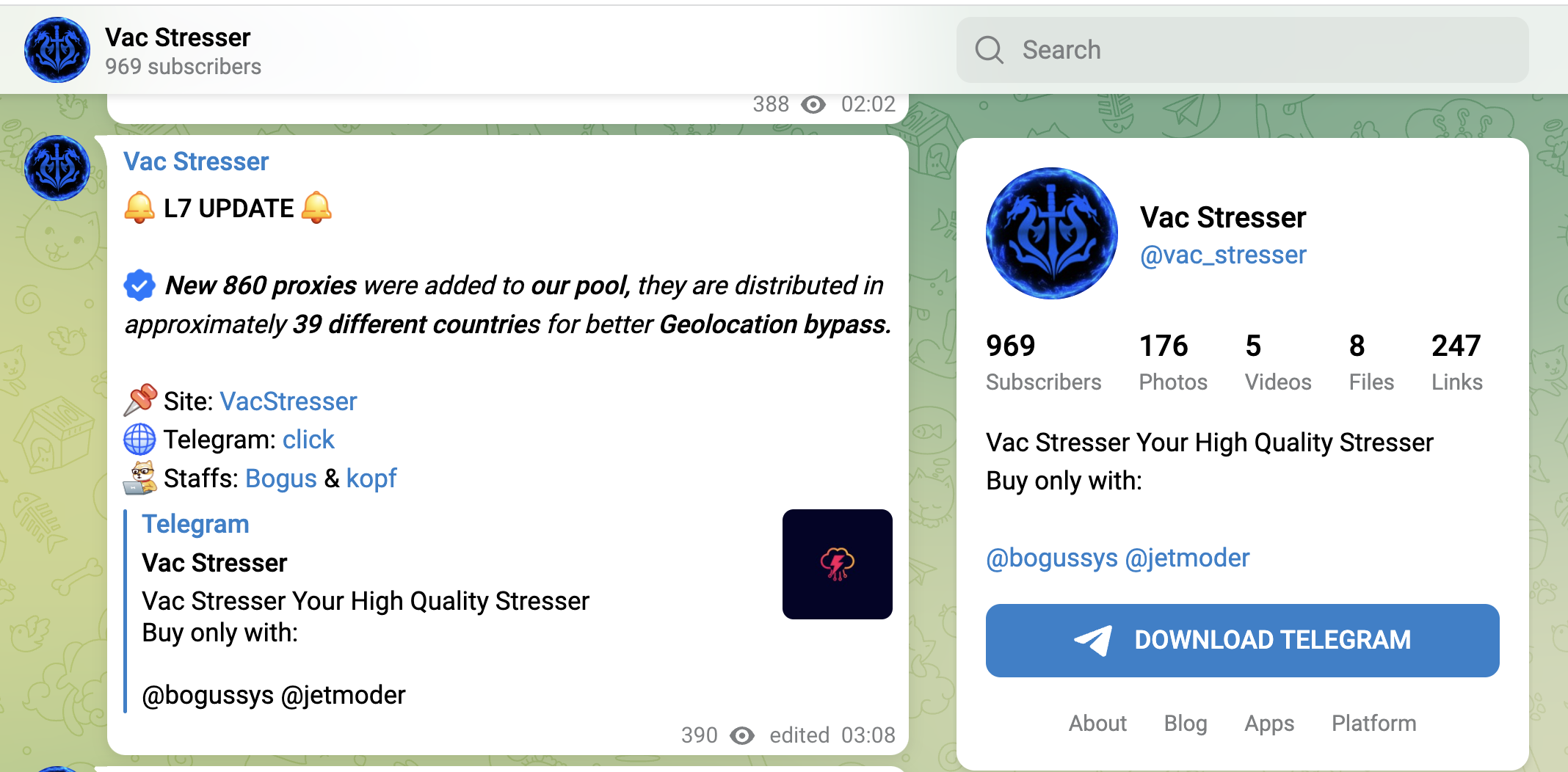
Now we see a trend to navigate around GeoIP-Restrictions by using various proxy-services and the ability to select country/region-based origins (screenshots below). That technique isnt new, and we described how threat actors used these method in our "Bypassing GeoFencing in advanced Layer-7 DDoS Attacks" - article, but now it is available in lower level booterservices as well.
Blueteamers: if your defense was mainly Geofencing, be prepared that this fence might fall soon
Example-screenshots take lately as of oktober 2023


Member discussion: